A researcher has used a free tool that he created and open source intelligence (OSINT) to demonstrate how easy it is for adversaries to gather intelligence on critical infrastructure in the United States.
The researcher, known online as Wojciech, used his Kamerka tool to find industrial control systems (ICS) in the United States, map them to geographical locations, and identify critical infrastructure targets that could be of interest to a threat actor. He believes the U.S. government should also conduct these types of tests to identify possible targets of potentially damaging attacks.
Kamerka
Kamerka is an open source tool that Wojciech launched in November 2018. The tool was initially designed to identify nearby surveillance cameras exposed to the internet, and it was later updated to allow users to also generate an interactive map of Flickr and Instagram photos, printers, and Twitter messages based on their geographical coordinates.
Version 3 of Kamerka, rolled out by the researcher in June, allows users to generate a map of exposed ICS in a specified country and link results to Google Street View. Version 4 introduced support for RTSP (Real-Time Streaming Protocol) and MQTT (Message Queue Telemetry Transport), which, according to the researcher, is often used by critical infrastructure organizations.
When the ICS features were introduced, Wojciech demonstrated his tool’s capabilities by showing exposed industrial systems in Poland and Switzerland.
The researcher has now made some further changes to the tool and tested it on industrial systems in the United States. The expert was scheduled to detail his findings at SecurityWeek’s ICS Cyber Security Conference in Atlanta later this month, but unfortunately he will not be able to present due to visa issues.
Exposed ICS devices in the United States
Kamerka uses Shodan to scan the internet for ICS devices and protocols, including Siemens S7, Tridium, General Electric, Mitsubishi Electric, Omron, PC WORX, Red Lion, Modbus, BACnet, HART-IP, DNP3, EtherNet/IP, Codesys, ProConOS and IEC 60870–5–104. The BinaryEdge search engine was used in support of the research.
The search showed roughly 26,000 internet-exposed ICS devices in the United States. The data was stored by the researcher in an Elastic database, which makes it easier to manage large amounts of data.
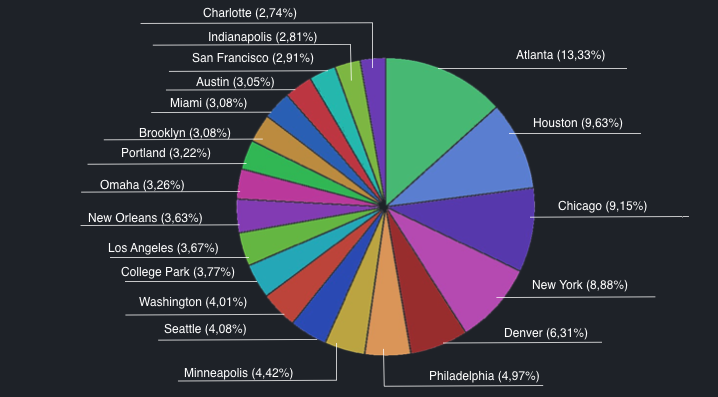
According to the researcher, the U.S. cities that house the highest percentage of these devices are Atlanta, Houston, Chicago, New York, Denver, and Philadelphia.
The most commonly found open ports used for ICS are 1911, 47808, 4911, 502 and 44818, which are associated with building automation systems (BACnet and Tridium’s Fox tunneling protocol), Modbus and EtherNet/IP. The FBI issued an alert last year to warn organizations about the risks associated with leaving port 1911 unprotected.
While many of the exposed systems are known to have vulnerabilities — it’s well known that it often takes organizations a lot of time to deploy available patches on industrial systems — Wojciech has pointed out that these systems can often be accessed using default credentials that are widely known.
The researcher has also identified exposed login pages, administration panels and human-machine interfaces (HMIs), including ones used by US government organizations, that can be accessed on non-ICS ports 80 and 8080 (HTTP).
Gathering intelligence on US critical infrastructure
This type of OSINT gathering can be highly useful to adversaries looking to conduct reconnaissance on a country’s critical infrastructure and Wojciech’s Kamerka tool and his research show how easy it is for adversaries interested in targeting critical infrastructure in the United States.
The researcher has selected five search results to prove his point. The first result is related to a Tridium Niagara system whose “station.name” parameter suggests that it is housed by a wastewater plant in Burlington, Vermont.
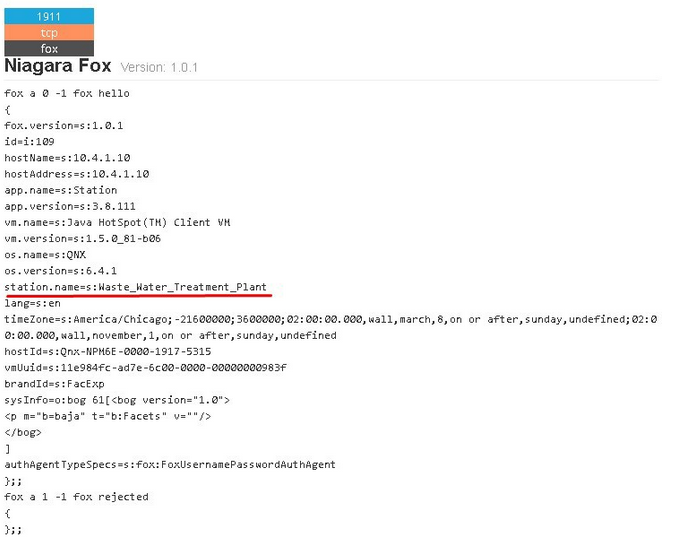
The results showed by Kamerka via Shodan place the device 1.5 miles from the actual plant — geolocation data is not very precise — but the search results also include other information that can be used to track down the exact building housing the exposed system. This can include the name of the street and even the name of the facility.
“Having this information, the next step would be to prepare physical surveillance and active intelligence gathering by scanning the asset and looking for more in the network,” the expert said.
Hackers have been known to target water utilities in the United States and experts have warned that these types of attacks could have serious consequences.
Wojciech has also analyzed another Niagara system housed by an organization in the pharmaceutical sector. In this case, the search result included the exact name of the organization and the general location, allowing the researcher to easily determine the facility’s exact location and find it on Google Maps. The impacted facility, located in Rockland County, New York, is one of the nine major R&D sites of Pfizer, one of the world’s largest pharmaceutical companies.
Another example targets the healthcare sector. The expert uncovered a building automation system made by Trane housed by Piedmont Hospital in Georgia. The geolocation data inaccurately showed that the device was located several miles away from the hospital, but the search results included the organization’s exact address.
Exposed Niagara systems were also found in a power plant in Winston-Salem, North Carolina, and a facility in Pennsylvania owned by defense contractor Lockheed Martin.
Once an adversary has pinpointed a facility’s location on Google Maps, they can obtain additional information about it from Google Search and often from the organization’s official website. The information can be useful in determining if the facility housing the exposed ICS is a potentially valuable target.
The researcher says he has reached out to each of these organizations, but none of them have responded.
Wojciech has admitted that some of the results may be honeypots set up by researchers to track threat actors targeting ICS. However, he believes that in most cases these systems are exposed due to misconfigurations and technicians wanting to make it easier for them to remotely access devices.
“These facilities provide equipment or services that ensure the continuity of the country and play an important role for society. In the case of commercial industries, it’s their own role to secure the network, but if it’s about critical infrastructure it’s in the public’s interest to keep it safe,” the researcher explained.
He added, “Special focus should be applied by utilizing intelligence gathering methods on your own country’s critical infrastructure to know what information can be collected by threat actors.”
Wojciech told SecurityWeek that he plans on launching a free web application that will make it easier to use Kamerka, including to conduct scans, manage results, and filter out non-critical devices.
UPDATE. Wojciech has published a blog post detailing his research on the ICS Cyber Security Conference blog.













