The patch released recently by VMware for a privilege escalation vulnerability affecting Fusion for Mac have been found to be incomplete.
VMware informed customers on March 17 that Fusion, Remote Console (VMRC) and Horizon Client for Mac are affected by a high-severity privilege escalation vulnerability caused by the improper use of setuid binaries. The company released updates that should have patched the vulnerability, which is tracked as CVE-2020-3950.
However, the researchers credited for reporting the vulnerability to VMware — Jeffball from cybersecurity firm GRIMM and Rich Mirch — both told SecurityWeek that the patch for Fusion is incomplete. Shortly after, VMware updated its initial advisory to confirm that Fusion 11.5.2 for macOS does not completely prevent exploitation.
The virtualization giant said the next Fusion release will contain a complete fix. In the meantime, users have been provided instructions on how to manually fix the problem to prevent potential exploitation. Users will have to install version 11.5.2 and then follow the steps described by VMware in its KB78294 article.
Mirch told SecurityWeek that his original proof-of-concept (PoC) exploit, which he has made public this week, works without any modification against Fusion 11.5.2.
“VMware USB Arbitrator Service and Open VMware Fusion Services are both setuid root binaries located at /Applications/VMware Fusion.app/Contents/Library/services,” Mirch explained in his PoC exploit. “When executed outside of the standard path the binaries can be tricked into executing a program from a path that the attacker controls. This is achieved by creating a hard link to the original binary. The binaries use part of the attacker-controlled path when executing the service and do not correctly validate that the target binary is legit.”
Jeffball, who has also published technical information about the flaw, told SecurityWeek that the “Open VMware Fusion Services binary is fixed, but the Open VMware USB Arbitrator Service binary is not. When running the exploit for fusion services, it gets a bad code signature error, but the same thing works fine on the USB arbitrator service.”
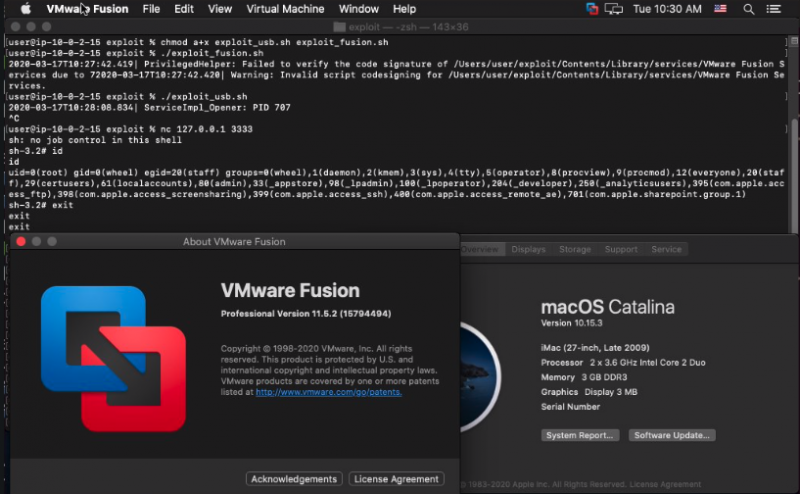
The updates for VMRC and Horizon Client appear to efficiently patch the vulnerability.
Related: VMware Patches Serious Flaws in vRealize Operations for Horizon Adapter
Related: Vulnerabilities Found in VMware Tools, Workspace ONE SDK
Related: VMware Patches ESXi Vulnerability That Earned Hacker $200,000














