The LockBit ransomware group claims to have stolen valuable SpaceX files after breaching the systems of piece part production company Maximum Industries.
The Texas-based Maximum Industries specializes in waterjet and laser cutting and CNC machining services, and advertises itself as a contract manufacturing facility.
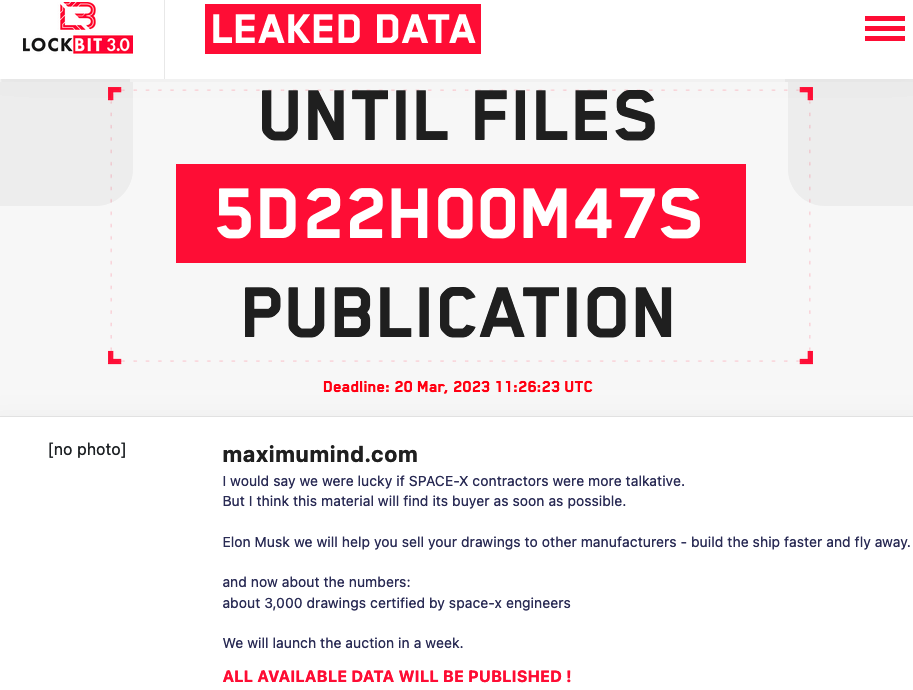
The LockBit hackers claim Elon Musk’s rocket and spacecraft maker SpaceX uses Maximum Industries services. They also claim that on Maximum Industries’ systems they found roughly 3,000 “drawings certified by space-x engineers”, which they plan on selling through an auction.
SecurityWeek has reached out to both SpaceX and Maximum Industries for comment, but none of them have responded.
While Maximum Industries may have been hacked, it’s not uncommon for cybercrime groups to make exaggerated claims regarding the impact of their attacks or the value of the data they have obtained.
The LockBit ransomware operation was launched in 2019 and it has been evolving ever since. The cybercriminals, believed to be operating out of Russia, exploit unpatched vulnerabilities, rely on insiders, or acquire access from specialized groups to gain access to victim systems. Once they have access, they collect valuable data, after which they deploy file-encrypting malware.
For more than a year now, LockBit has been the most active ransomware operation. To date it has targeted well over 1,000 organizations, including major companies such as German car parts giant Continental.
Related: New ‘Exfiltrator-22’ Post-Exploitation Framework Linked to Former LockBit Affiliates
Related: Russian National Arrested in Canada Over LockBit Ransomware Attacks
Related: LockBit Ransomware Site Hit by DDoS Attack as Hackers Start Leaking Entrust Data

















