Easy Mobile Cloud Server Management with Free Rackspace Cloud Pro for iPad Application
RackSpace Hosting (NYSE:RAX), today announced the release of Rackspace Cloud Pro™, a new application for Apple’s iPad™ to enable users to monitor and manage their Rackspace Cloud Servers™.
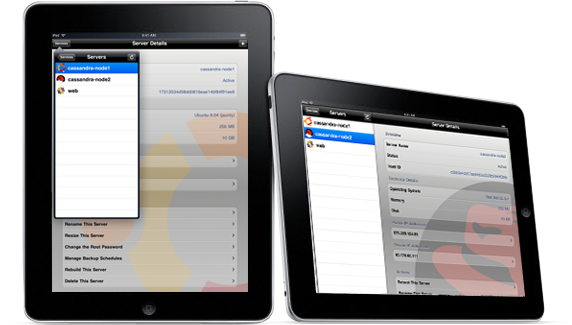
The features built into Cloud Pro for iPad allow RackSpace Cloud customers to:
- Rename Cloud Servers
- Resize Cloud Servers
- Perform Hard Reboots
- Perform Soft Reboots
- List all the Cloud Servers on their account
- View details about each Cloud Server
- Manage backup schedules for Cloud Servers
- Create new Cloud Servers (including from any existing backups)
- View Rackspace Cloud system status as a whole
- Ping public IP address and see how responsive a Cloud Server is from 41 different locations
- Launch SSH Server (assuming user has an SSH app such as iSSH that supports launching via URL)
Cloud Pro for iPad frees businesses and developers from their desktops by offering them enterprise-quality server control and functionality through the convenience and mobility of the iPad.
“As we build out our cloud, we expect to become more visible around the issues of openness, data access and customer choice,” stated Lew Moorman, President Cloud and Chief Strategy Officer, Rackspace Hosting. “Our goal is to allow our customers to be able to choose the services, applications, databases and OSs they want to use in a non-proprietary environment without the fear of being locked into one particular cloud. Our Cloud Server mobile management capability for the iPad is the latest example of Rackspace’s leadership in driving open cloud innovation.”
For more information and to download the app visit: http://www.rackspacecloud.com/ipad














