The minds behind the Nitro attacks discovered targeting chemical companies earlier this year are at it again. But this time, they have added a new twist – they are disguising malware as an attachment from Symantec.
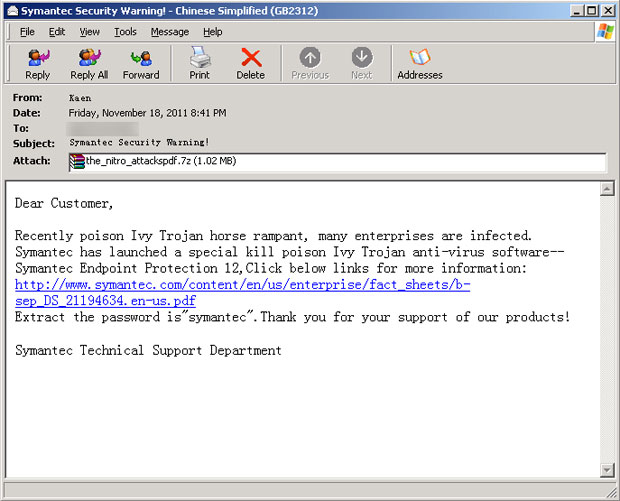
The emails, which portend to come from the Symantec Technical Support Department, are titled ‘Symantec Security Warning!’ and contain an attachment with a variant of Poison Ivy – the remote administration tool (RAT) which has been at the heart of the cyber-campaign since it was first detected several months ago.
According to Symantec, the attachment itself is called “the_nitro_attackspdf.7z.” When the self-extracting executable runs, it creates a file called lsass.exe (Poison IVY) and creates a PDF file. Ironically, the PDF file is Symantec’s own document on the Nitro attacks.
“The Nitro attacks have not changed targets or intensity since our initial report went public,” said Vikram Thakur, principal security response Manager at Symantec. “This fact is actually what spurred the update we released on these attacks today. It demonstrates the brazen attitude the attackers have towards law enforcement, corporations being attacked, security researchers and any other groups that have an interest in stopping this threat.”
In April, the attackers behind Nitro went to work targeting human rights organizations. They then moved on to the auto industry. By July, they had switched gears to chemical companies. Other industries were targeted as well, and the highest percentages of victims as of October resided in the United States and Bangladesh.
“Despite the publishing of the whitepaper, this group persists in continuing their activities unchecked,” blogged Symantec researchers Tony Millington and Gavin O’Gorman. “They are using the exact same techniques – even using the same hosting provider for their command and control (C&C) servers. The domains have been disabled and Symantec have contacted the relevant IP hosting provider and continue to block the emails through the .cloud email scanning service.”
















