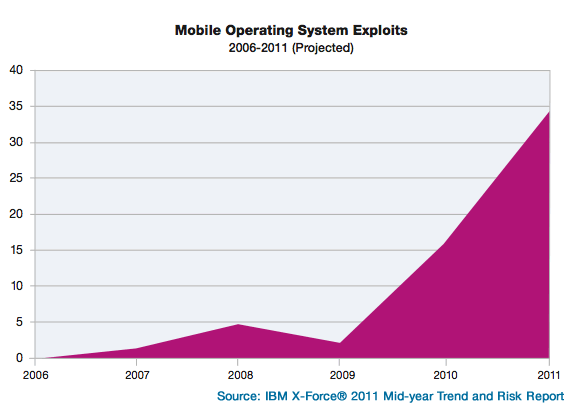
IBM researchers are predicting 2011 will see twice as many mobile exploits as 2010.
In a new report, IBM’s X-Force team declares the consumerization of IT – epitomized by the “Bring Your Own Device” approach becoming commonplace among companies – is raising security concerns due to the steady rise in security vulnerabilities and malware affecting these devices. Their declaration echoes findings from Damballa, which noted a significant increase in the number of Android devices infected with malware during the first half of the year.
“For years, observers have been wondering when malware would become a real problem for the latest generation of mobile devices,” said Tom Cross, manager of Threat Intelligence and Strategy for IBM X-Force, in a statement. “It appears that the wait is over.”
According to the report, mobile malware is typically delivered through third-party app stores. However, infected applications have also been found on applications on peer-to-peer networks, hosted on Websites and even on Usenet.
“These off-market applications are usually targeted at people looking for pirated versions of commercial Android applications,” the report’s authors wrote.
While the report noted the increase in mobile threats, the researchers also found that the first half of 2011 saw a decrease in Web application vulnerabilities, which dropped from 49 percent of all vulnerability disclosures down to 37 percent. This is the first time in five years X-Force reported seeing a decrease. In addition, high and critical vulnerabilities in web browsers were also at their lowest point since 2007.
IBM researchers tested almost 700 web sites — from the Fortune 500 and other most popular sites – and discovered that 40 percent of these contain client-side JavaScript vulnerabilities. Meanwhile, the success of advanced persistent threats (APTs) raised the profile of “whaling” –spear phishing targeting large organizations, the researchers said.
“The rash of high-profile breaches this year highlights the challenges organizations often face in executing their security strategy,” Cross said. “Although we understand how to defend against many of these attacks on a technical level, organizations don’t always have the cross-company operational practices in place to protect themselves.”
In related news, IBM also said that it is launching the Institute for Advanced Security in Asia Pacific, in order to combat growing security threats in the region. The IBM Mid-Year X-Force report states that top countries originating spam have shifted to Asia Pacific, with India sending out roughly 10 percent of all spam registered today, and South Korea and Indonesia also making the top five list. This Institute joins IBM Institues in Brussels, Belgium and Washington, D.C.
The full X-Force Report is available here. (PDF Download)
Related Reading: Attacks on Mobile and Embedded Systems: Current Trends












