An Office vulnerability patched by Microsoft last year has been exploited by several advanced persistent threat (APT) actors in operations aimed at organizations in Asia, Kaspersky Lab’s Global Research and Analysis Team reported on Wednesday.
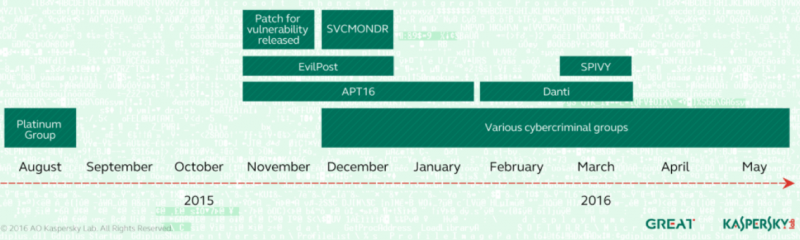
The remote code execution flaw, tracked as CVE-2015-2545, had been exploited by an APT group dubbed Platinum and TwoForOne before Microsoft released a patch in September 2015 and a more comprehensive fix two months later. The actor, which has been known to target organizations in South and Southeast Asia, has been active since at least 2009.
CVE-2015-2545 can be exploited for arbitrary code execution via specially crafted Encapsulated PostScript (EPS) image files inserted into Office documents. The exploit for this flaw can evade Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP) mitigations.
According to Kaspersky Lab, Platinum was the first group to exploit the vulnerability to deliver malware, but the threat actor apparently stopped using it after Microsoft released patches.
One of the first APT groups to start leveraging CVE-2015-2545 after it was fixed by Microsoft is EvilPost, a China-linked gang that used weaponized Word documents to attack a Japanese defense contractor in December 2015.
At around the same time, a different Chinese attacker dubbed APT16 used an exploit for this Office vulnerability to target media and government agencies in Taiwan. Organizations in Taiwan were also targeted in December 2015 by a threat actor dubbed by Kaspersky “SVCMONDR.”
The SVCMONDR attacks share similarities with operations carried out by a group called Danti. However, researchers have not been able to precisely determine if SVCMONDR and Danti are the same group or if they simply used the same malicious code.
Danti is an actor that has been observed targeting entities in Kazakhstan, Kyrgyzstan, Uzbekistan, Myanmar, Nepal and the Philippines. It’s believed to be a new group that is related to the NetTraveler and DragonOK cyberspies, whose activities were analyzed in 2013 and 2014.
Danti used CVE-2015-2545 in February and March to launch attacks against Indian diplomatic organizations, including many embassies. The group’s activities were also analyzed recently by Palo Alto Networks, which found connections between the malware used in the attacks aimed at Indian embassies and malware used in 2013 in a campaign called Operation Ke3chang. Evidence suggests that the attackers are located in China.
Palo Alto Networks recently also analyzed a campaign where an APT group leveraged the Office flaw to deliver a Poison Ivy variant named “SPIVY” to organizations in Hong Kong.
According to Kaspersky, all of these groups have exploited CVE-2015-2545 to target entities in Asia — none of them have been observed attacking organizations in Western Europe or the United States.
In addition to APT actors, traditional cybercriminals have also leveraged the Office exploit in mass spam campaigns.
“Such attacks mostly target financial institutions in Asia. Specifically, attacks have been recorded in Vietnam, the Philippines and Malaysia. There are reasons to believe that Nigerian cybercriminals are behind these attacks. In some cases, the infrastructure used is the same as the one we saw when analyzing the Adwind Trojan,” researchers said in a blog post.
















