Is an Internet Kill Switch Possible in the United States?
 With the recent events in Egypt and the debate over proposed legislation, “Cyber Security and American Competitiveness Act of 2011”, the term “Internet Kill Switch” has flashed into popular discussion. So what does the term mean, what does it look like, and can it be really be done?
With the recent events in Egypt and the debate over proposed legislation, “Cyber Security and American Competitiveness Act of 2011”, the term “Internet Kill Switch” has flashed into popular discussion. So what does the term mean, what does it look like, and can it be really be done?
Last week, Wired reported that the “Kill Switch” bill will introduce legislation that would give the US government power to limit Internet traffic in the event of cyber-security emergency. The intent of the bill is to provide a mechanism for the government to work with the private sector to respond swiftly to a significant threat. It is not a mandate to be able to shut down the entire Internet but rather authorizes the president to order access to “critical infrastructure” be turned-off.
 Our interest here is to look at just one dimension of the issue – the technical feasibility; the political and policy aspects, we’ll leave to others.
Our interest here is to look at just one dimension of the issue – the technical feasibility; the political and policy aspects, we’ll leave to others.
To recap recent events in Egypt, public political protests reached critical mass on January 25th. As in Iran, the use of social media contributed to the visibility and tempo of the situation. On January 27th, Internet connectivity and access across the region began plummeting ultimately leading to a five-day blackout. Service resumed February 2nd, but not before inflicting major losses to the Egyptian economy.
The 60-day monitor and tracking chart below clearly demonstrates the pattern of performance and impact to one of Egypt’s 91 autonomous systems. Note the period of instability before the end of the month, then the sharp spike in ‘CIDR deletions’, which effectively removed these IP blocks from the routing tables used by ISPs, thereby rendering them unreachable.
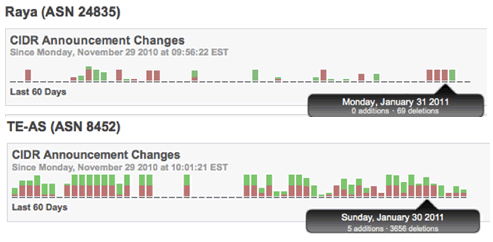
Egypt’s actions follow other recent government ordered blackouts as seen in Myanmar and Iran. In each case, an autocratic government could assert control over a relatively small number of major ISPs (ASNs – Autonomous System Numbers). Flipping the switch was achieved by changes to the routing tables (CIDR deletions) used by the ISPs.
The question remains….. could the same approach be taken in the US? The ubiquitous and interconnected nature of the United States ISPs, and the reliance of the critical infrastructure sectors within the U.S. on those ISPs coupled with the lack of overall visibility present enormous technical challenges. Below are three to consider:
1) Master complete visibility and understanding of the Internet – In order to control, direct, or limit routing, which is essentially what would be required, the government would have to have visibility and a solid understanding of all Internet assets and their routing commands. When considering the global Internet, you must have the ability to view it, map it, and track it from multiple perspectives and vantage points. If this is not achieved, you could never be sure closing access in one area would not open access via another, nor could you be sure to maintain operations of those assets you wish not to impact.
2) Overcome the size and scale of the countries Internet presence – The table below, generated from a routing database, gives an appreciation for the difference in scale between the US and these other countries.
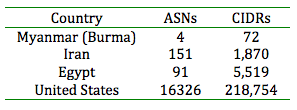
When one considers the difference in scale of ownership and governance between the US government infrastructure and these other countries, it is hard to infer that the US government could induce a blackout to the same effect as these other cases.
3) Own the ability to take action – An effective surgical response requires sensing and validating the cyber-emergency from multiple sources, sharing the appropriate notice and responsibility with critical infrastructure partners and relevant agencies, and managing a distributed means to synchronize, execute, and monitor the shut down activity.
Until these challenges are overcome, a technical solution will be out of reach – even if a political solution is enacted.













