Securing the Extended Enterprise
As corporations expand their reliance on the Internet and technology to conduct business, most work diligently to reduce their exposure to attack. Their efforts are focused primarily on protecting their enterprise assets, but could they be missing a very important aspect of their attack surface…. the extended enterprise?
The attack surface is defined as the exposure area that remains reachable and vulnerable to attack. This includes any accessible area where weakness provides an opportunity to exploit. As an analogy, when a martial artist squares off against an opponent, he positions himself in a way that best reduces his attack surface. He must consider his entire body as part of the attack surface. He shifts his stance, maintains balance, positions his arms and hands up in order to protect his vital points. While everyone has their fair share of vulnerabilities, those that are successful in protecting themselves, do a better job minimizing their exposure. As fighters move through the ring, they continually need to make adjustments to protect themselves. Defense requires diligence, persistence, and both a broad and deep view of potential exposure and compromise since even the most obscure weakness may cause harm.
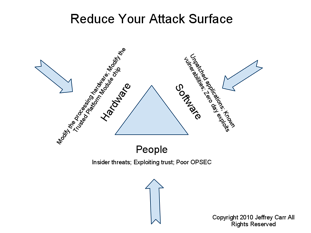
When relating this concept to network security, engineers and managers must consider the entire extended enterprise network part of the attack surface. As depicted in the accompanying figure, this includes hardware, software, and people. The network security manager must know where they are susceptible to attack in order to protect themselves. This requires a good bit of visibility and understanding of both the enterprise and extended enterprise. While most corporations have emphasized enterprise security management over the last decade, they have often overlooked vulnerabilities incurred by partner’s, provider’s, supplier’s, vendor’s and customer’s networks, all of which must be considered when defining and protecting the extended enterprise. Your extended enterprise IS part of your attack surface.
The challenge with defense is you have to cover all possible weaknesses, while the attacker really only needs to find and exploit one.
Conducting business today requires speed and interconnectivity. We operate globally by transmitting data from hop to hop across the global Internet, across provider networks and to final destinations all in which we rely heavily upon, we do not control or manage, and where we have very little insight. Just as important are the relationships and physical and logical connections we make with these entities. Without any control or insight, how do we expect to limit our attack surface or minimize our risk when we don’t in many cases know or have visibility into what we even need to protect?
Similarly, consider the military supply chain during wartime. The ability to get beans, bullets, and Band-Aids to the troops depends not only on the local field commanders but also on potentially dozens of hops along the way to include sea ports, ships, aircraft, airports, etc – all outside of the field commanders control but still critical in his ability to accomplish his mission. Visibility into the security and viability of those waypoints may not be available to that commander because they are out of his control, but problems or issues along the way will assuredly impact him. It stands to reason that the longer and more complex the supply chain, the greater the attack surface and more likely it would be compromised.
The extended enterprise is often overlooked in this analysis, however it can be quite impactful. Vulnerabilities incurred by partners, providers, suppliers, vendors, and in some cases customers often extend the attack surface for businesses and introduce unrealized and unacceptable risk.
The attack surface of an enterprise is directly proportional in size to its reach across the Internet. It’s vulnerability to botnet, phish, malware, hi-jacking (BGP, DNS, etc), and DDoS expands and it’s reliance upon security technology, processes, and people servicing the extended enterprise become greater. This reliance increases exposure to unpatched applications, known vulnerabilities, insider threats, poor operations security, physical security, and the list goes on. Situational awareness becomes a critical aspect of doing business. Observing activity, connections, and threats associated with the extended enterprise is core to limiting the attack surface and protecting today’s business operations. Correlating the knowledge of on-goings beyond enterprise boundaries with internally monitored activity may expose hints of malicious activity and threats. Understanding these dependencies requires having the right analysis tools and the right data sources. Neglecting this process may result in an unacceptably vulnerable attack surface. A mistake that can hardly be afforded.
Jeff Carr, CEO of GreyLogic and author of “Inside Cyber Warfare: Mapping the Cyber Underworld,” contributed to this article.














