Intel has paid out more than $4.1 million through its bug bounty program since its creation in 2017, according to a product security report published by the chip giant on Wednesday.
Between 2018 and 2021, Intel paid out, on average, $800,000 through its bug bounty program each year for vulnerabilities discovered in the company’s products. In 2022, it awarded $935,000.
Intel says a total of 243 vulnerabilities were reported in 2022, roughly the same as in the previous three years. More than half of the 2022 vulnerabilities were found internally by the company and 90 security flaws, representing 37% of the total, were reported via its bug bounty program.
The company engaged 151 researchers last year, more than double compared to the previous three years.
Most of the vulnerabilities were discovered in Intel software, processors, and network communications products. Only two issues were assigned a ‘critical’ severity rating, but 79 were classified as having ‘high’ severity.
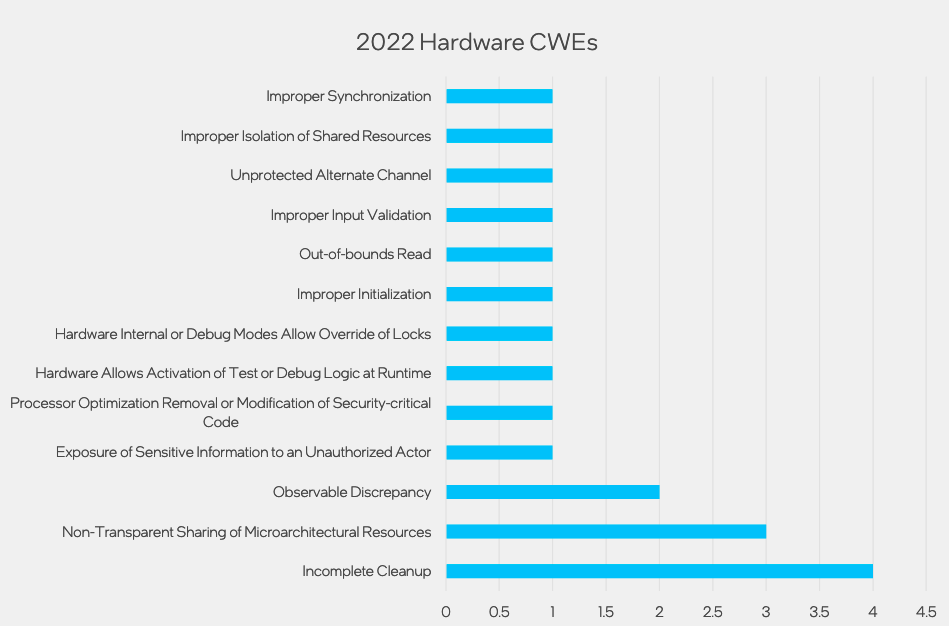
Intel has helped create a hardware common weakness enumeration (CWE) list and 19 of the hardware vulnerabilities addressed last year were assigned to 13 hardware CWEs.
“To deliver security at scale, we have over 500 dedicated product security staff, perform over 120 hackathons per year, fund 40+ academic research teams, and continue to expand our Bug Bounty programs in innovative ways,” Intel said.
The Intel Product Security Report details several of the company’s cybersecurity initiatives.
Related: Dozens of Vulnerabilities Patched in Intel Products
Related: Intel Confirms UEFI Source Code Leak as Security Experts Raise Concerns
Related: Intel Patches Severe Vulnerabilities in Firmware, Management Software














