New research suggests that the number of governments using the controversial FinFisher spyware suite has increased.
FinFisher is a lawful interception solution developed by Germany-based FinFisher GmbH and sold exclusively to governments. Researchers have been monitoring the use of FinFisher over the past years and found it in many countries, including ones that have a poor human rights and civil liberties record, such as Bahrain and Ethiopia.
Researchers at Citizen Lab, an interdisciplinary laboratory based at the Munk Centre for International Studies at the University of Toronto in Canada, have identified new ways to determine the physical location of FinFisher servers.
According to experts, FinFisher customers are provided a master server (FinSpy Master) and multiple relays (FinSpy Relay) whose purpose is to act as command and control (C&C) servers. The FinFisher spyware deployed on victims’ devices communicates with the relay servers, which provide a link to the master server.
A scan conducted by Citizen Lab using the Zmap tool revealed the existence of 135 servers, which includes both FinSpy Masters and Relays. The master servers are deployed on the customer’s premises so identifying their location exposes governments that use FinFisher. The proxies are located in other countries as their purpose is to protect the location of the master.
While the developers of FinFisher claim relays make it “practically impossible” to discover the location of the master servers, Citizen Lab has found a way to use these proxies to determine the real location of the master.
If the IP address of a FinSpy Relay is entered into a web browser, the user is usually presented with a decoy page, often Google.com or Yahoo.com. If the decoy page is Google, researchers can perform a search for “my ip address” and the search engine will display the real IP address of the FinSpy Master. That happens because the search request goes through the Relay to the Master, which in turn queries Google and sends the result back to the Relay, which displays it to the user conducting the “my ip address” search. Since the query is made by the Master, Google will return its IP address and not the one of the Relay.
This technique doesn’t work in the case of Yahoo, but Citizen Lab has found an alternative method to obtain location information. While in the case of Yahoo researchers haven’t managed to obtain exact IP addresses, the webpage’s source code contains location data because Yahoo uses it to display customized weather information and news on the homepage.
Some of the other decoy pages identified by experts also revealed IPs or location data.
Citizen Lab noticed that the number of servers returning decoy pages has decreased over time, most likely because FinFisher or its customers have realized that they can be problematic.
Using the aforementioned techniques, experts identified FinFisher users in 32 countries. In addition to previously known customers, 16 new countries have been identified, including Angola, Egypt, Gabon, Jordan, Kazakhstan, Kenya, Lebanon, Morocco, Oman, Paraguay, Saudi Arabia, Slovenia, Spain, Taiwan, Turkey, and Venezuela. In some cases, researchers were able to trace the identified IP addresses to specific government organizations, but some information has been redacted in Citizen Lab’s report to avoid interference with legitimately sanctioned activities.
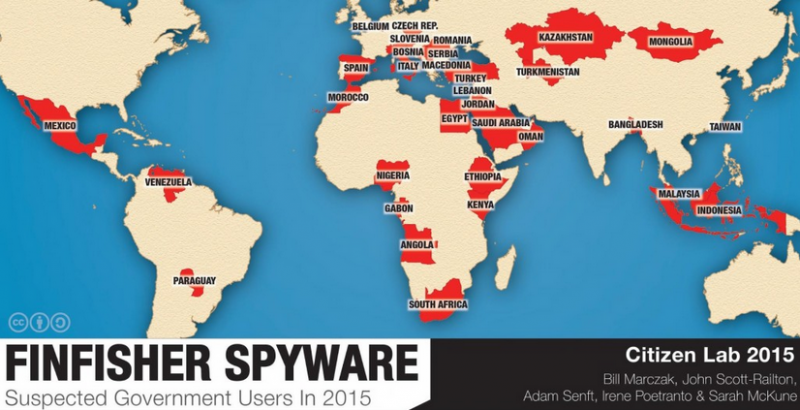
“A key goal of this research is to provide a resource to those working on policy and research in this space. We also believe this kind of reporting is essential to help ensure that citizens have the opportunity to hold their governments accountable,” Citizen Lab said in its report.
FinFisher’s systems were breached last year and tens of gigabytes of data were leaked online. However, the incident doesn’t appear to have had too much of an impact on the company’s operations.
Hacking Team, a FinFisher rival based in Italy, was also hacked this year presumably by the same attacker. Just like FinFisher, Hacking Team also seems to be confident that the breach will not have a negative impact on business, despite the fact that hackers leaked source code, exploits, and private communications.












