Enterprise data fusion and analytics company Gravwell on Wednesday emerged from stealth mode with $3 million in seed funding from Next Frontier Capital, Gula Tech Adventures, Kickstart Fund, and Revolution’s Rise of the Rest.
Gravwell has developed a platform that is designed to enable security teams to investigate, collaborate, and analyze data from any source. The platform is advertised as being very useful for threat hunting.
The Coeur d’Alene, Idaho-based company says that unlike other solutions, which limit the amount of data that can be collected and analyzed, the Gravwell platform offers unlimited data ingestion, unlimited environments, unlimited data retention, and unlimited endpoints “at a cost that doesn’t break your budget.”
Gravwell has three pricing plans: Pro Edition (starting at $500/month), Enterprise Edition (starting at $24,000/year) and Enterprise Extended (starting at $48,000/year). The company claims that its enterprise plans offer analytics capabilities for which some organizations currently pay two or three times as much.
Gravwell says its platform enables organizations to search petabytes of data in seconds, with its largest deployment analyzing more than 100 terabytes of data per day. The company says its platform’s live dashboards provide real-time insight, and enable customers not only to look at their data, but also “play” with it, without having to worry about breaking something.
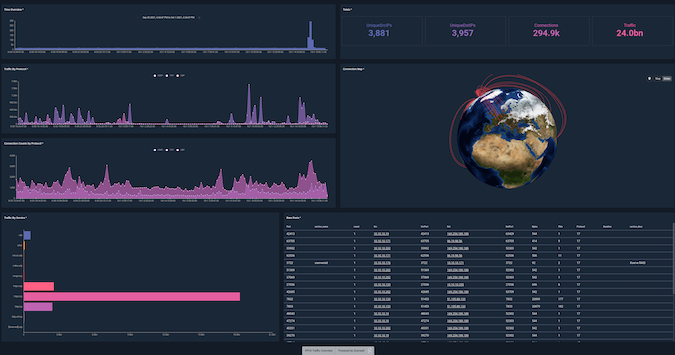
“We are incredibly proud of the value that we deliver for our customers,” said Gravwell CEO Corey Thuen. “There are very few tools that actually scale past 40 terabytes per day, and no one is collecting all the data they want. On our platform, they will never have to make a decision about which data to use or lose, it is ALL their data.”
Related: Data Security Startup Code-X Emerges From Stealth With $5 Million in Funding
Related: Neosec Emerges From Stealth With $20.7 Million in Funding
Related: MSSP SolCyber Emerges From Stealth With $20 Million Series A Funding
Related: SaaS Security Company Grip Security Emerges From Stealth














