Google’s Project Zero cybersecurity research unit on Thursday announced that it’s making some changes to its vulnerability disclosure policies, giving users 30 days to install patches before disclosing the technical details of a flaw.
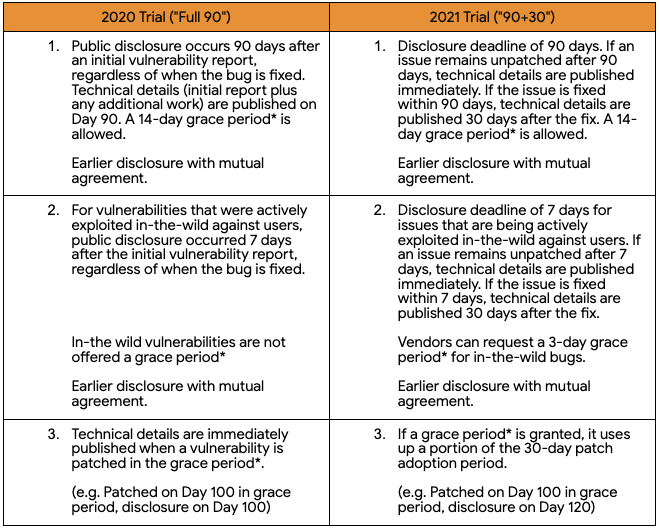
Project Zero has announced three major changes to its vulnerability disclosure policy in 2021, compared to 2020. Until now, if Project Zero researchers found a security hole in a product, it was disclosed after exactly 90 days, regardless of when a patch was released or whether a patch was available at all. The impacted vendor could request a 14-day grace period and disclosure could happen earlier based on a mutual agreement.
For 2021, the disclosure deadline of 90 days remains unchanged, but if the vulnerability is patched within that 90-day timeframe, technical details will only be made public 30 days after the release of a fix, to give users time to install the patch. The 14-day grace period can still be requested by the vendor.
In the case of actively exploited vulnerabilities, technical details have been disclosed 7 days after the initial report, even if the bug hasn’t been fixed, and vendors could not request a grace period before disclosure.
Starting now, if the vendor manages to patch the vulnerability within 7 days, technical details will only be disclosed 30 days after the fix is released. The goal is to give users more time to install the patch and avoid scenarios where other threat actors could use the disclosed information for their attacks. In addition, vendors will be able to request a 3-day grace period for vulnerabilities exploited in the wild.
Another change is related to disclosure during the 14-day grace period. Until now, a vulnerability was disclosed immediately by Project Zero if a patch was released after the standard 90-day deadline but within the 14-day grace period. From now on, if the vendor is granted a grace period, Project Zero will wait for up to 30 days before releasing details to give users time to install the patch. The number of days in the grace period before a fix is released will be subtracted from the 30-day patch adoption period. For instance, if a vulnerability is patched on day 100 during the grace period, the vulnerability will be disclosed on day 120.
Project Zero says the goals of its policies are faster patch development, thorough patch development (i.e. ensure a patch is complete), and improved patch adoption.
The debate surrounding vulnerability disclosures focuses on whether releasing technical details faster is more beneficial to defenders, who can use the information to assess risk and implement defensive measures, or attackers, who can leverage the disclosed vulnerabilities in their attacks.
“From our time in the defensive community, we’ve seen firsthand how the open and timely sharing of technical details helps protect users across the Internet. But we also have listened to the concerns from others around the much more visible ‘opportunistic’ attacks that may come from quickly releasing technical details,” Tim Willis, senior security engineering manager at Project Zero, wrote in a blog post.
“We continue to believe that the benefits to the defensive community of Project Zero’s publications outweigh the risks of disclosure, but we’re willing to incorporate feedback into our policy in the interests of getting the best possible results for user security,” Willis added.
While the latest changes provide some advantages to users and vendors, Project Zero says it’s aware that the 90+30 day policy will make it more difficult for defenders “to quickly perform their own risk assessment, prioritize patch deployment, test patch efficacy, quickly find variants, deploy available mitigations, and develop detection signatures.”
Related: Exploit for Second Unpatched Chromium Flaw Made Public Just After First Is Patched
Related: Google Starts Tracking Zero-Days Exploited in the Wild
Related: Google: Sophisticated APT Group Burned 11 Zero-Days in Mass Spying Operation












