The final version of the 2017 OWASP Top 10 was released on Monday and some types of vulnerabilities that don’t longer represent a serious risk have been replaced with issues that are more likely to pose a significant threat.
The Open Web Application Security Project (OWASP) announced the first release candidate for the 2017 OWASP Top 10 back in April, and there has been a lot of debate about what should and what should not be included.
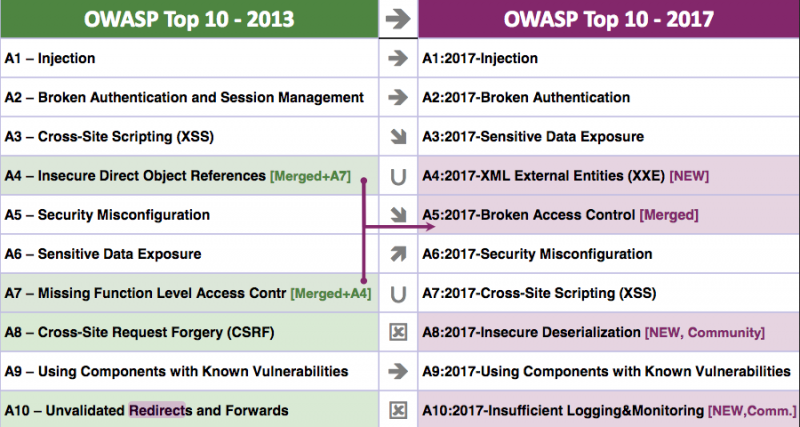
One significant change compared to the 2013 OWASP Top 10 is the fact that the types of flaws that made it into the 2017 list have been selected based on the risk they pose.
The OWASP Top 10 vulnerabilities are injection, broken authentication, sensitive data exposure, XML external entity (XXE), broken access control, security misconfiguration, cross-site scripting (XSS), insecure deserialization, using components with known vulnerabilities, and insufficient logging and monitoring.
While XSS can be classified as a type of injection, the decision has been made to leave it in a separate category as these types of bugs are addressed differently compared to SQL and OS command injections.
Cross-site request forgery (CSRF) has been removed from the OWASP Top 10 as modern development frameworks ensure that such vulnerabilities are avoided, which has led to CSRF being found in less than 5% of applications. Unvalidated redirects and forwards have also been removed as they affect only around 8% of apps.
Insecure direct object references (IDOR) and missing function level access control have been merged into broken access control.
The free spots were filled by XXE, insecure deserialization, and insufficient logging and monitoring. Critical deserialization flaws have been found in several high profile apps in the past few years so it’s not surprising that it made the list. As for logging and monitoring, OWASP pointed out that many organizations have serious problems in this department, as clearly demonstrated by the significant number of breaches discovered by third-parties instead of the targeted organization itself.
OWASP also noted that while the names of some categories have not changed, the types of issues they cover has changed. For instance, sensitive data exposure refers to privacy and personal information exposure, not leaky headers and stack traces, and misconfigurations now also include cloud-related issues such as unprotected storage containers (e.g. AWS S3 buckets).
The 2017 OWASP Top 10 is based on data from 23 contributors covering more than 114,000 applications. The data has been made available on GitHub, a move that is part of OWASP’s efforts to be more transparent.
After a break, OWASP will start working on the next Top 10, which has been scheduled for 2020.















