Some users may be able to recover the files encrypted by the Bad Rabbit ransomware without paying the ransom, Kaspersky researchers discovered after analyzing the malware’s encryption functionality.
Once it infects a device, Bad Rabbit looks for certain file types and encrypts them. The disk is also encrypted and a ransom screen is displayed when the computer boots, preventing the victim from accessing the operating system. The disk encryption and bootloader functionality are provided by code derived from a legitimate utility named DiskCryptor.
Bad Rabbit has been linked to the NotPetya attack that caused significant disruptions to many companies back in late June. However, unlike NotPetya, which experts classified as a wiper due to the fact that victims could not recover their files even if they paid the ransom, files encrypted by Bad Rabbit can be recovered with the right decryption key.
While the encryption mechanisms used by the attackers, AES-128-CBC and RSA-2048, cannot be cracked, Kaspersky experts have identified some methods that may allow some victims to decrypt their disk and recover files.
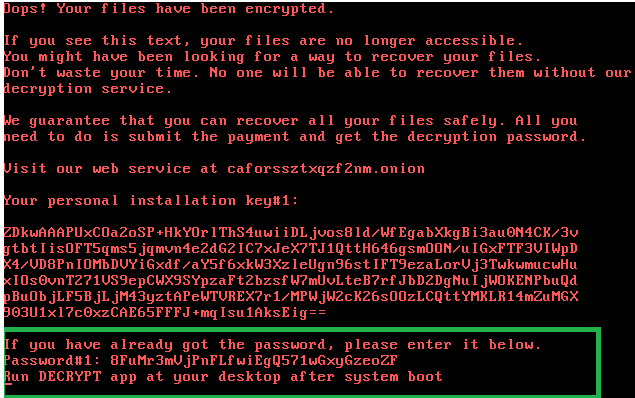
When an infected computer boots up, users are informed that their files have been encrypted and they are instructed to make a payment in order to obtain the password needed for decryption. The same screen also allows victims who have already obtained a password to enter it and boot their system.
Kaspersky researchers discovered that the password needed to boot the system is not wiped from memory after it’s generated, giving users the opportunity to extract it before the process that creates the password, dispci.exe, is terminated. Entering this password boots the system and decrypts the disk, the security firm told SecurityWeek, but there is only a “slim chance” that victims will actually be able to extract the password.
As for recovering files, experts noticed that Bad Rabbit does not delete shadow copies, which are backups made by Windows. If users enabled this backup functionality before the files were encrypted and the malware’s full disk encryption functionality failed for some reason or the disk is decrypted using the aforementioned method, the data can be restored via Windows or third-party utilities.
Kaspersky has also confirmed that Bad Rabbit does in fact use an NSA-linked exploit to spread; earlier reports claimed no exploits had been observed. The malware uses EternalRomance, which NotPetya also leveraged.
Based on the numerous similarities, the Bad Rabbit attack is believed to have been carried out by the same threat group that launched the NotPetya campaign, namely the Russia-linked threat actor known as BlackEnergy, TeleBots and Sandworm Team. Some are not convinced due to the fact that a majority of the victims were in Russia. Others pointed out, however, that the main target may have been Ukraine, where several major organizations were hit.
Related: Profiling Tool Suggests ‘Bad Rabbit’ Not Financially Motivated
Related: ‘Bad Rabbit’ Attack Infrastructure Set Up Months Ago













