Several major organizations in Russia and Ukraine were hit in the past few hours by a ransomware named “Bad Rabbit.” The incident reminds of the massive attack involving NotPetya malware, which ended up costing companies millions of dollars.
Few details are known so far about the Bad Rabbit attack, which has the potential to cause significant damage.
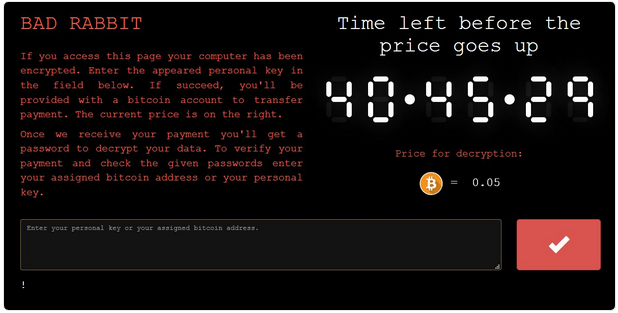
Infected computers display a screen informing users that their files have been encrypted and instructing them to access a website over the Tor anonymity network. The Tor site tells victims to pay 0.05 bitcoin, worth roughly $283, to obtain the key needed to recover the encrypted files. However, the price goes up if the ransom is not paid within two days.
The list of organizations reportedly hit by the Bad Rabbit ransomware includes Russian media outlets Interfax and Fontanka, the airport in Odessa, the Kiev subway, the State Aviation Service of Ukraine, and the Transport Ministry of Ukraine. Interfax and others said the attack disrupted their operations.
Researchers are still analyzing the malware, but initial reports claim Bad Rabbit has been distributed via fake Flash Player updates. Some said the ransomware also leverages the Mimikatz post-exploitation tool for lateral movement within the compromised network. Kaspersky’s Anton Ivanov revealed that the threat uses code from a legitimate disk encryption utility named DiskCryptor.
Security firm ESET said the malware appears to be a new variant of NotPetya, also known as Diskcoder, Petya, Petrwrap, exPetr and GoldenEye. However, this has not been confirmed by other researchers. ESET reported that while most infections are in Russia and Ukraine, some compromised machines were also detected in Turkey, Bulgaria and other countries.
There are also some reports that Bad Rabbit uses SMB – specifically the NSA-linked EternalBlue exploit – to spread, just like NotPetya. However, this hasn’t been confirmed either.
The attack does remind of NotPetya, which started spreading via a software update from a Ukrainian company. However, NotPetya turned out to be a wiper instead of ransomware.
The fact that another major attack has hit Ukraine is not surprising considering that the country’s Security Service warned earlier this month about a possible large-scale cyberattack on state organizations and private companies. The agency said the purpose of the attack would be to disrupt IT systems and destabilize the situation in the country.













