Finland-based cybersecurity firm F-Secure on Thursday announced the launch of a new endpoint detection and response (EDR) solution that combines human expertise and artificial intelligence.
The new offering, F-Secure Rapid Detection & Response, is designed to help organizations protect their IT systems against targeted attacks.
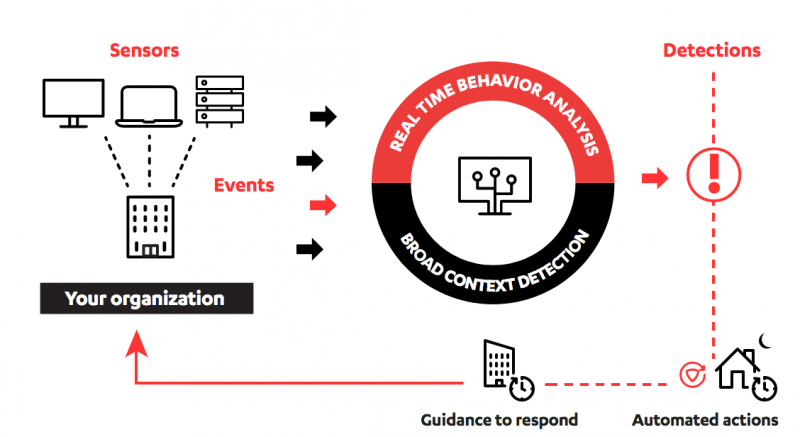
The solution leverages lightweight endpoint sensors and AI-powered data analysis capabilities to monitor devices for malicious activity. Rapid Detection & Response creates a baseline for normal behavior and flags any unusual activity. Suspicious behavior is subjected to additional analysis to prevent false positives that could overwhelm security teams, F-Secure said.
The product can be configured to respond to potential threats in various ways. It can provide guidance to the organization’s IT team or managed service provider on how to respond to an incident, or it can take action automatically in order to contain an attack. More difficult cases can be escalated to a local partner that is trained and supported by F-Secure experts.
Each potential threat is analyzed using a process that F-Secure has named Broad Context Detection, which leverages both human expertise and AI to help organizations validate threats and assess their impact.
“One trick that’s common in modern attacks is to disguise malicious activity as something normal, and attackers are always finding new ways to do this. And since there’s countless numbers of normal things happening in any given environment, it’s basically impossible for companies to rely on human experts or artificial intelligence alone to comb through all that data,” explained F-Secure Chief Technology Officer Mika Stahlberg.
“Artificial intelligence trained by the best cyber security experts is vital when you’re looking for needles in a digital haystack, and in the right hands, it’s able to keep defenders a step ahead of even the most skilled, highly motivated attackers,” Stahlberg added.
F-Secure Rapid Detection & Response is available through the security firm’s network of authorized partners. The solution can be managed directly by an organization’s IT department or it can be used as a managed service from one of F-Secure’s partners.
Related: UK’s 1E Challenges Tanium With New Endpoint Detection & Response (EDR) Tool
Related: Mitre ATT&CK Matrix Used to Evaluate Endpoint Detection and Response Product
Related: Microsoft Brings Windows Defender ATP to Windows 7, 8.1










