A new piece of malware discovered a few months ago by researchers at ESET provides more evidence that Industroyer (aka Crashoverride) is linked to the NotPetya wiper.
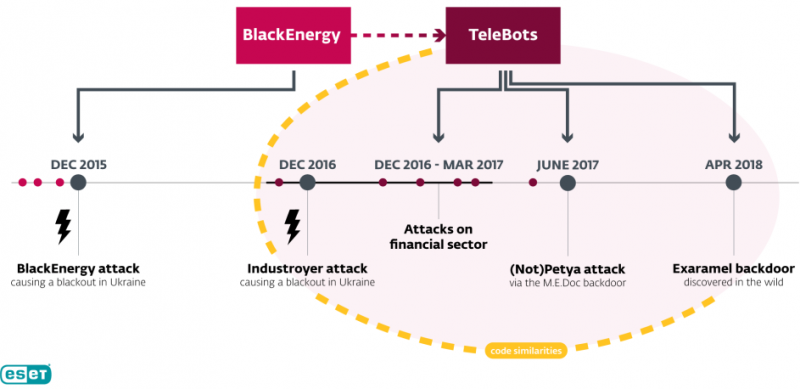
Industroyer is a piece of ICS-focused malware that was used by threat actors in the December 2016 attack aimed at an electrical substation in Ukraine, which resulted in significant power outages.
Experts have found links between this attack and various threat groups believed to be operating out of Russia, including BlackEnergy, TeleBots, Sandworm, and Electrum. The campaigns attributed to BlackEnergy, TeleBots, Sandworm, and Electrum could have been carried out by one or multiple groups, but overlaps in code, infrastructure and targeting have often made it difficult to make a clear distinction between their activities.
NotPetya — initially believed to be a piece of ransomware and later proven to be a wiper — has also been linked by researchers to BlackEnergy and KillDisk malware, which had been used in the 2015 attacks on Ukraine’s energy sector.
While there are several pieces of evidence that support the theory of a connection between NotPetya and BlackEnergy, the link between Industroyer and the Russian groups is mainly based on components that are similar in concept rather than actual code similarities.
However, a new piece of malware uncovered by ESET in April 2018, tracked by the company as Exaramel, provides stronger evidence of a connection between Industroyer and TeleBots.
Exaramel, which ESET has classified as a backdoor, is delivered by a dropper. The configuration data written by the dropper in the Windows registry includes the security solution used on the compromised system, which reminds of Industroyer.
Once executed, the backdoor can allow the attackers to launch processes, write data to a file, upload files, execute shell commands, and run VBS code. Researchers have found significant similarities in the code implementing some of the commands in Exaramel and a backdoor from the Industroyer toolset.
Another similarity is related to the fact that both Exaramel and the Industroyer backdoor use a report file to store the output of executed shell commands and processes.
According to ESET, the main difference between Exaramel and Industroyer is that the former uses the XML format for communication and configuration instead of a custom binary format. Anton Cherepanov, senior malware researcher at ESET, told SecurityWeek that the main advantage of using XML is that it’s much easier to implement code that would use this format.
Cherepanov noted that while there are some other differences between these pieces of malware, they are not that different from a high level perspective.
The expert told SecurityWeek that ESET has only seen one attack involving Exaramel — aimed at an organization in Ukraine. It’s interesting to note that the target was not an industrial facility.
Industrial cybersecurity firm Dragos revealed earlier this year that the threat group behind Industroyer, which it tracks as Electrum, had started targeting entities outside of Ukraine, including organizations in the water and electric sectors.
ESET has identified two samples of the Exaramel backdoor, along with various other tools used by the attackers. Some of these tools have been seen in previous attacks launched by TeleBots, including a modified version of Mimikatz and a custom password stealer named CredRaptor. During incident response, ESET also uncovered a Linux backdoor, which the company tracks as Linux/Exaramel.A.
“The strong code similarity between the Win32/Exaramel backdoor and the Industroyer main backdoor is the first publicly presented evidence linking Industroyer to TeleBots, and hence to NotPetya and BlackEnergy. While the possibility of false flags – or a coincidental code sharing by another threat actor – should always be kept in mind when attempting attribution, in this case we consider it unlikely,” ESET said in a blog post published on Thursday.
ESET also noted that the attackers had started using domain names that appeared to be related to the security firm. This was most likely done in an effort to hide malicious traffic.















