The energy sector was targeted by cyberattacks more than any other industry, and many of the vulnerabilities disclosed last year impacted products used in this sector, according to a report published on Monday by Kaspersky Lab.
The security firm has analyzed a total of 322 flaws disclosed in 2017 by ICS-CERT, vendors and its own researchers, including issues related to industrial control systems (ICS) and general-purpose software and protocols used by industrial organizations.
Of the total number of security holes, 178 impact control systems used in the energy sector. Critical manufacturing organizations – this includes manufacturers of primary metals, machinery, electrical equipment, and transportation equipment – were affected by 164 of these vulnerabilities.
Other industries hit by a significant number of vulnerabilities are water and wastewater (97), transportation (74), commercial facilities (65), and food and agriculture (61).
Many of the vulnerabilities disclosed last year impacted SCADA or HMI components (88), industrial networking devices (66), PLCs (52), and engineering software (52). However, vulnerabilities in general purpose software and protocols have also had an impact on industrial organizations, including the WPA flaws known as KRACK and bugs affecting Intel technology.
Learn More at SecurityWeek’s ICS Cyber Security Conference
As for the types of vulnerabilities, nearly a quarter are web-related and 21 percent are authentication issues.
A majority of the flaws have been assigned severity ratings of medium or high, but 60 weaknesses are considered critical based on their CVSS score. Kaspersky pointed out that all vulnerabilities with a CVSS score of 10 are related to authentication and they are all easy to exploit remotely.
Kaspersky said 265 of the vulnerabilities can be exploited remotely without authentication and without any special knowledge or skills. It also noted that exploits are publicly available for 17 of the security holes.
The company has also shared data on malware infections and other security incidents. In the second half of 2017, Kaspersky security products installed on industrial automation systems detected nearly 18,000 malware variants from roughly 2,400 families. Malware attacks were blocked on almost 38 percent of ICS computers protected by the company, which was slightly less than in the second half of the previous year.
Again, the energy sector was the most impacted. According to the security firm, roughly 40 percent of the devices housed by energy organizations were targeted.
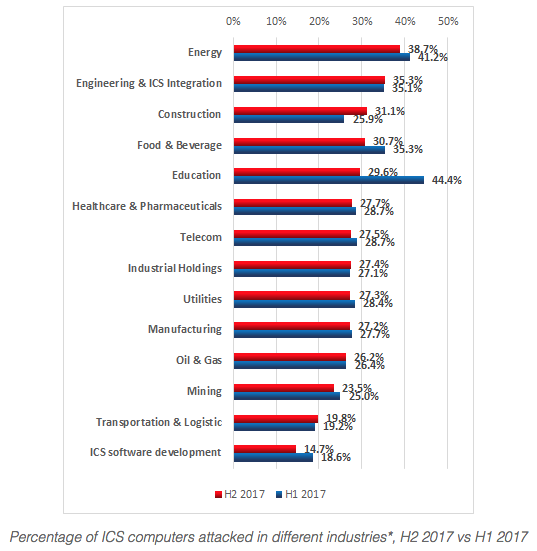
“In the vast majority of cases, attempts to infect ICS computers are accidental and are not part of targeted attacks,” Kaspersky said. “Consequently, the functionality implemented in malware is not specific to attacks on industrial automation systems. However, even without ICS-specific functionality, a malware infection can have dire consequences for an industrial automation system, including an emergency shutdown of the industrial process.”
One example was the WannaCry attack, which, according to Kaspersky, in some cases resulted in temporary disruptions to industrial processes.
Researchers noted that botnet agents can also pose a significant threat, including by stealing sensitive data and by causing disruptions to industrial processes as a side effect of coding errors and incompatibility. Kaspersky reported that last year more than 10 percent of the systems it monitored were targeted by botnet agents.
Related: Oil and Gas Sector in Middle East Hit by Serious Security Incidents
Related: Increasing Number of Industrial Systems Accessible From Web
Related: Non-Targeted Malware Hits 3,000 Industrial Sites a Year














