Instrumentation and process automation company Endress+Hauser has patched a vulnerability affecting many of its field instruments.
The problem is an improper input validation vulnerability (CVE-2014-9191) in the CodeWrights HART Device Type Manager (DTM) library, which is used by several industrial control system (ICS) vendors. The flaw was discovered last year by researchers at Russia-based Digital Security.
CodeWrights addressed the vulnerability with the release of a new version of the library not long after researchers reported its existence. Endress+Hauser has started integrating the new library in its products.
An attacker can exploit the flaw to crash HART-based devices, but ICS-CERT noted in an advisory published this week that the vulnerability is difficult to exploit.
The security hole affects Cerabar, Deltabar, Deltapilot, Gammapilot, iTemp, Levelflex, Liquicap, Liquiline, Micropilot, Multicap, Omnigrad, Nivotester, Promag, Promass, Prosonic, Prothermo, Prowirl, and other transmitters and devices from Endress+Hauser.
One of the first ICS vendors to start using the patched CodeWrights library was Emerson, which announced the integration of the new library in January.
Alexander Bolshev, one of the Digital Security researchers involved in this project, told SecurityWeek in January that this is a medium to low risk vulnerability that can only be exploited by an attacker that has physical access to the targeted system.
“To trigger the vulnerability, the attacker should have an ability to alter the packet on the way from the field device to the DTM component. How it could be done depends on the actual ICS infrastructure. E.g. this could be done by MiTMing the field device on the HART current loop (if the attacker has access to it) or forging the packet when it’s going through gateways to the DTM component,” Bolshev explained at the time.
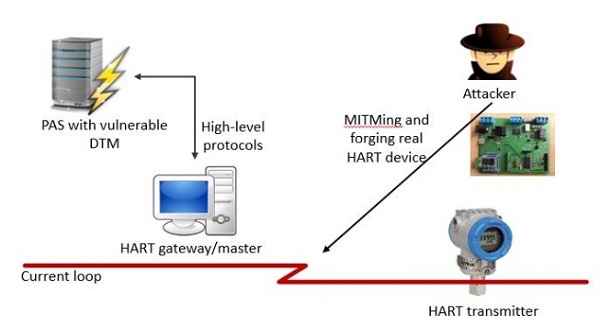
“The actual impact of the vulnerability is the Denial of Service of the DTM component, FDT [Field Device Tool] frame application and other DTM components in the same container,” the researcher added. “Based on the real infrastructure, the restart of the FDT Frame application or rebooting the server with the FDT Frame may be needed to recover the system.”
Advisories from ICS-CERT show that Honeywell, Magnetrol and Pepperl+Fuchs also started integrating the new version of the CodeWrights library into their products at the beginning of this year.
The CodeWrights vulnerability was identified by Digital Security as part of a larger research project targeting vulnerable DTM components. Experts identified a total of 32 vulnerable DTM components from 24 vendors.














