Attacks targeting operational technology (OT) infrastructure increased by over 2000 percent in 2019 compared to the previous year, and the piece of malware most commonly seen in these attacks was the Mirai variant named Echobot, IBM revealed on Tuesday.
IBM’s 2020 X-Force Threat Intelligence Index summarizes the most prominent threats observed by the company’s researchers last year, including OT threats.
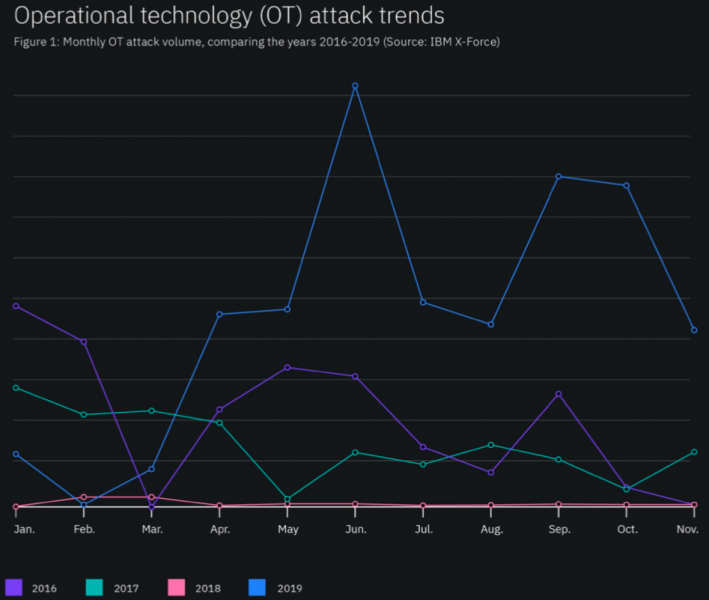
Based on data derived from network event logs, IBM saw an increase of over 2000 percent in attacks targeting industrial control systems (ICS) and other OT assets compared to 2018.
“In fact, the number of events targeting OT assets in 2019 was greater than the activity volume observed in the past three years,” the company said in its report.
According to IBM, most of the OT attacks involved exploitation of known vulnerabilities and password-spraying attempts.
Some of the observed activity was linked to well-known threat actors. One of them was XENOTIME, the group behind the 2017 Triton/Trisis malware attack on a Saudi Arabian petrochemical plant, which last year started targeting electric utilities in the United States and the APAC region. The Iran-linked threat actor tracked as APT33 (aka Hive0016, Elfin, and Holmium) also reportedly started targeting ICS last year.
However, Charles DeBeck, cyber threat intelligence expert at IBM, told SecurityWeek that the “primary offending malware” observed in ICS attacks was Echobot, which is a variant of the notorious Mirai IoT malware. Echobot emerged last year and it has incorporated over two dozen different exploits, including ones targeting enterprise and ICS products.
Learn More About ICS Threats at SecurityWeek’s 2020 ICS Cyber Security Conference
The ICS-specific exploits used by Echobot target CVE-2019-14931, an unauthenticated remote OS command injection vulnerability affecting Mitsubishi Electric ME-RTU devices, and CVE-2018-7841, a remote command execution flaw affecting Schneider Electric’s U.Motion Builder product.
DeBeck said the ICS attacks were primarily focused on the manufacturing industry and they had a wide geographical distribution.
“EchoBot is a well documented and long-running malware variant with multiple capabilities. We are seeing sustained volumes of attacks and it’s interesting to see that this broad-based malware is getting in on the action of targeting OT systems, suggesting a broader interest in this space,” DeBeck explained.
However, the expert said IBM had not seen any Echobot attacks where the malware caused disruptions or other serious problems for the affected organizations.
The data analyzed by IBM for its latest report covers only attacks that were specifically targeting OT. “While these attacks may have been widespread, their targeting against OT was specific,” DeBeck noted.
IBM has observed a decrease in ICS attacks since early October 2019, but the company expects to see a rise in these types of incidents in 2020.
“X-Force expects that attacks against OT/ICS targets will continue to increase in 2020, as various threat actors plot and launch new campaigns against industrial networks across the globe. With more than 200 new ICS-related CVEs released in 2019, IBM X-Force’s vulnerability database shows that threats to ICS will likely continue to grow in 2020,” the company wrote in its report.
Related: Study Analyzes Challenges, Concerns for IT/OT Convergence
Related: Non-Targeted Malware Hits 3,000 Industrial Sites a Year















