More than half of U.S. government agencies have fully implemented the DMARC email security standard in response to a binding operational directive from the Department of Homeland Security, according to email threat protection company Agari.
The DHS issued the Binding Operational Directive (BOD) 18-01 in mid-October 2017, instructing all federal agencies to make plans and start using web and email security technologies such as HTTPS, STARTTLS and DMARC.
DMARC (Domain-based Message Authentication, Reporting and Conformance) is an email authentication, policy, and reporting protocol designed to detect and prevent email spoofing. Organizations can set the DMARC policy to “none” to only monitor unauthenticated emails, “quarantine” to send them to the spam or junk folder, or “reject” to completely block their delivery.
Agencies were given one year to fully implement DMARC (i.e. set their DMARC policy to “reject”).
Agari has been monitoring more than 1,000 government domains to check their status. Shortly after the DHS issued the BOD, only 18% had implemented at least a minimal DMARC policy. By December 2017, nearly half had rolled out DMARC, but only 16% had set a “quarantine” or “reject” policy.
Agari’s latest report shows that 922 government-owned domains, representing 81% of the total, had enabled DMARC as of July 15. Nearly 600, representing 52%, have set a “reject” policy.
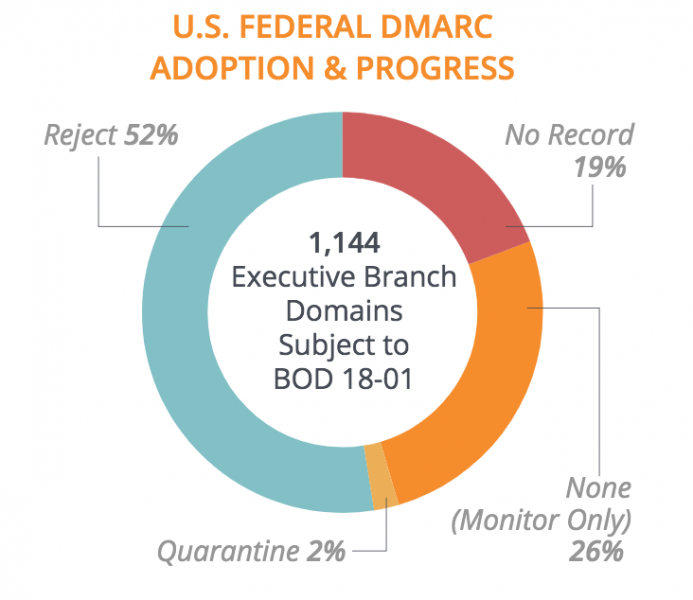
While this may seem like significant progress, Agari pointed out that two-thirds of the domains with a “reject” policy are “defensive domains,” which are not configured for sending email.
“Moving defensive domains to a DMARC enforcement policy is generally an easier process than moving active domains that send email, and also need to account for 3rd parties sending email on the agency’s behalf as well as specific mail servers permitted to send email,” Agari said in its report.
The company has determined that 28 agencies have fully protected all their domains. Some government organizations still have some unprotected assets, but they have secured a significant number of domains.
For example, the Department of Health and Human Services has enabled DMARC with a “reject” policy on 92 of its 118 domains, while the Department of Justice has done so for 65 of its 75 domains.
“To fully reach compliance with BOD 18-01, and to protect the federal government from phishing attacks, many more executive branch agencies must still implement ‘p=reject.’ But in comparison to the private sector, the U.S. Government should serve as a shining example for the implementation of common security standards,” Agari said.
Related: DMARC in Higher Education – A Formidable Defense Against Targeted Scams
Related: DMARC Adoption Low in Fortune 500, FTSE 100 Companies














