Most reports on consumerization of technology, or “bring your own device,” are somewhat negative—at least from the view of IT and Security departments. We hear about all the threats, and challenges in managing multiple device types, enabling these devices on corporate networks and maintaining security and control over the devices and what goes on them.
The bottom line is that employees are demanding access corporate networks, applications, and information anywhere at any time with any device and managing this isn’t always easy. However, as IT departments struggle to keep employees happy and empowered while managing risk, they are starting to see more benefits from the trend of employees brining their own devices to the workplace.
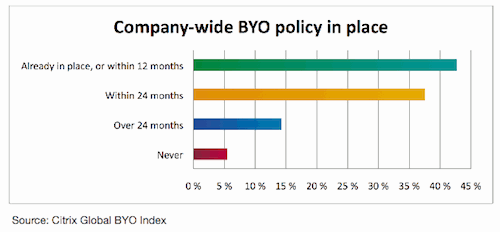
Citrix Systems yesterday released the results of the Citrix Bring-Your-Own (BYO) Index revealing that 92 percent of IT organizations are aware that employees are using their own devices in the workplace. and 94 percent intend to have a formal BYO policy in place by mid-2013, up from 44 percent today.
The research from Citrix discovered that attracting and retaining the highest quality talent, increased worker productivity and mobility and greater employee satisfaction, as well as reducing IT costs, are the primary drivers of BYO adoption.
According to Mick Hollison, there are two reasons that that this is a growing trend in organizations. “There are those that are using BYO to keep up with the rapid consumerization of enterprise IT and then there are forward-thinking CIOs who have embraced BYO as a way to attract the best talent, encourage a flexible working environment and raise productivity levels,” said Hollison, vice president, Desktop Marketing & Strategy, for Citrix.
No IT department wants a malware-laden laptop that is shared with teenagers combing the Internet and social networks floating around the office or accessing its network. So how can IT departments effectively manage risk with these devices that they can’t keep a close watch on?
According to Citrix, Desktop Virtualization is a key enabler. The BYO Index revealed that sixty two percent of surveyed organizations already invested or plan to invest in desktop virtualization, technology that allows organizations to manage Windows-based desktops centrally in the datacenter, then deliver them to all types of users across the enterprise. Eighty percent of those organizations intend to leverage their desktop virtualization investment to support employee-owned devices and BYO.
Desktop virtualization addresses two key challenges cited by survey participants – security and device management. By enabling IT to centrally manage and secure desktops, applications, and data in the datacenter, business information is always secure. Even when data is stored on the end point device, IT has the ability to remotely erase data in the event the device is lost or stolen.
Desktop virtualization makes it possible for IT to deliver desktops and apps straight from the datacenter to any device, making device management radically simpler. “Desktop virtualization enables IT to fundamentally rethink the way user hardware is provisioned by making a reliance on a limited number of corporate-standard PCs, laptops and smartphones a thing of the past,” stated Hollison. “It also provides a safe way of delivering a desktop to any employee, on any device, wherever they are, with the a consistent high definition user experience.”
Evolution of Devices will be a Driver
The survey also revealed that the types of devices used by workers will continue to evolve in the coming years. The most popular devices brought into the workplace today are the laptop and smartphone. However, most companies anticipate that within two years, the use of tablets like Apple’s red-hot iPad, as the primary personal computing device will rise significantly to almost 23 percent from just 8 percent today. IT decision-makers also believe they will need to manage a wide range of tablet platforms by 2013 including Apple iOS, Android, Blackberry and Windows. Desktop virtualization technologies will make it possible for IT to support this growing device diversity with a universal way to deliver desktops and apps from the datacenter.
Other Key Findings
• The primary benefits of BYO are improved employee satisfaction at 57 percent, increased worker productivity at 52 percent, greater mobility for workers at 51 percent, more flexible work environments for employees at 46 percent and reduced IT costs at 36 percent.
• Forty-four percent of organizations intend to pay employees a stipend roughly equivalent to the cost of its own IT department procuring and managing a comparable device and 31 percent plan to help offset some of the cost.
• Ninety four percent of IT decision makers indicated that the introduction of a BYO policy has predominantly been led by the IT department. They also noted that other departments are getting involved in the development of BYO policies with Human Resources participating in 39 percent of organizations, Legal in 35 percent and Finance departments in 29 percent.
The Citrix BYO Index is based on a survey of 700 IT professionals conducted in May 2011. One hundred IT professionals were surveyed in each of seven markets including: Australia, Canada, Germany, India, Netherlands, United States and United Kingdom. In each country, half of the respondents represented companies of 500-1,000 employees and the other half work for companies of 1,000+ employees.
The Full BYO Index report is available here. (PDF, No Registration Required)
Related Reading: IT Departments Struggle with Keeping Workers Happy and Empowered while Managing Risk











