The recently patched F5 BIG-IP vulnerability tracked as CVE-2022-1388 is being increasingly exploited by threat actors, including to “destroy” affected appliances.
CVE-2022-1388 is a critical remote code execution vulnerability that can easily be exploited by an unauthenticated attacker. Attacks can be launched from the internet against devices that expose their management interface — there are a few thousand such devices — or from the targeted organization’s network.
Patches and mitigations were announced on May 4 and the first attack attempts were spotted within days.
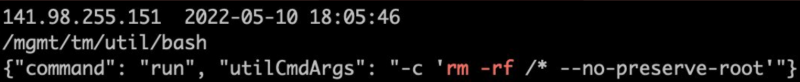
The SANS Technology Institute is one of the several entities that have seen attacks exploiting CVE-2022-1388, and the organization has observed attack attempts that involve a command for erasing files, “rm -rf”.
“Given that the webserver runs as root, this [command] should take care of any vulnerable server out there and destroy any vulnerable BIG-IP appliance,” SANS said on Twitter.
The latest destructive attack attempts involve the “no-preserve-root” option in the command, which is used for deleting the root file system with all data and binaries.
Researcher Kevin Beaumont, who has been monitoring the attacks, has confirmed that “real world devices are being erased,” noting that many of the internet-exposed systems seen via Shodan have stopped responding.
“I thought they were being remotely shut down but the threat actor is deleting the whole F5 file system, which is breaking load balancing and websites,” he explained.
[ READ: Technical Details, IoCs Available for Actively Exploited BIG-IP Vulnerability ]
Researcher Germán Fernández, one of the first to report seeing massive exploitation of the vulnerability, said that, as of Tuesday, more than 300 BIG-IP appliances had web shells installed by malicious actors. He advised users to scan their systems even if they’ve deployed the available patches as they may have been compromised before the fixes were installed.
Beaumont said a threat actor apparently operating out of Iran had been “spraying” web shells, and pointed out that the destructive attacks could have resulted in the hackers losing those shells.
Cisco’s Talos threat intelligence and research unit has also seen attack attempts exploiting CVE-2022-1388, and it has observed a slight increase in scans hitting the education sector. However, it admitted that the activity did not appear to be targeted.
Talos also noted that attackers may attempt to obfuscate their exploit code in an effort to evade detection.
Palo Alto Networks and GreyNoise have also seen scanning activity and exploitation attempts, but they had not seen destructive attacks by the time this article was published.
The US Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added CVE-2022-1388 to its Known Exploited Vulnerabilities Catalog. Federal agencies are required to address the flaw by May 31, but hopefully they have already rolled out patches or mitigations given the elevated risk.
BIG-IP application delivery controllers are used by some of the world’s biggest organizations — F5 says 48 of Fortune 50 companies are customers.
Related: Iranian Hackers Target Critical Vulnerability in F5’s BIG-IP
Related: CISA Says Hackers Exploited BIG-IP Vulnerability in Attacks on U.S. Government
Related: Vulnerability Exposes F5 BIG-IP Systems to Remote DoS Attacks













