Before I switched over to the vendor side, I was building cyber security programs for many years. In my previous role as a CISO there were so many different components to think about that the only way I could get some clarity was to build a mind map and start laying things out in an organized manner.
I started with our existing infrastructure and processes and built this out to how I thought everything fit together – and how it SHOULD work together. This helped provide a holistic view of our security capabilities and then deeper visibility into each area so we could see where we had gaps and where we had depth in terms of the people, processes and technology that we had at our disposal. Threat intelligence was a critical component that not only was part of the mind map, but we used intel to help influence and drive strategic decisions around how that mind map and cyber security program was constructed.
In a nutshell, every product and service your organization creates is dependent on technology in some way, shape or form in order to be successful. Threats to that technology translate into a higher likelihood of risks to those products and services. Intelligence helps you identify what threats are actively exploiting risks within your organization (the reactive aspect) as well as what threats are materializing on the horizon (the proactive aspect) so that you can best apply the proper resources to the proper problem.
So I thought it would be useful to explore cyber threat intelligence from this perspective to help other organizations get some clarity around intel, what it means to them and how it fits into their overall security strategy over the course of a series of articles as there is a lot to cover.
There is certainly no shortage of threat intelligence articles and opinions out there – with their own definitions of how things should be – but as someone who has walked the walk both as a CISO who has built programs and as a vendor in the threat intel space, I thought that “CTI in the mind of Adam” was worth sharing. Depending on your organization and how your cyber program is set up, some of the specifics here may or may not be as relevant – each org is different and while it’s always good to follow “best practices”, you also have to do what makes sense for your business.
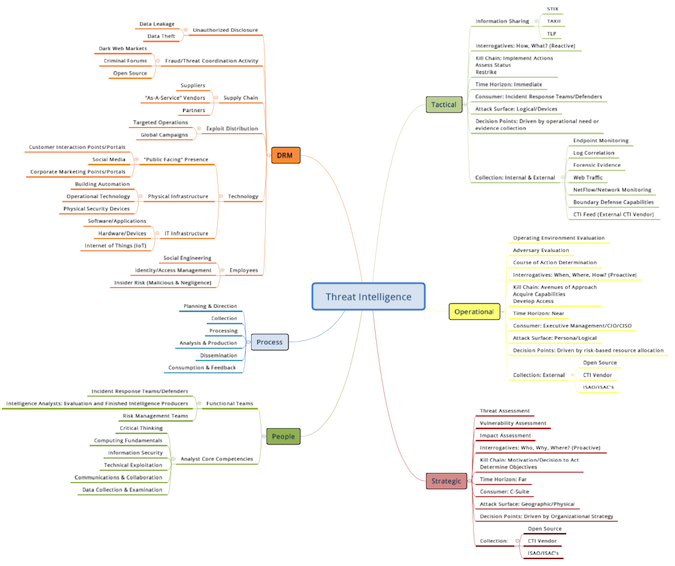
View Larger Image in New Window
On the right I’ve broken out the three different levels of CTI – tactical, operational and strategic.
• Tactical is basically the low level “on the wire” type of intelligence, generally called an Indicator of Compromise (IOC) which is typically a feed of malicious IPs, Domain, URL Hash strings. Etc. This is the reactive How & What?
• Operational intelligence generally focuses on the campaign and operations that are in use as it looks at capabilities, opportunities and intentions of threats – essentially the proactive When, Where and How?
• Strategic intel is where threats are coupled with organizational impact, taking more of a risk-based view that helps you align your security program to your threat reality. I.e. the proactive, Who, Why and Where?
On the left side I’ve broken out the people, process and Digital Risk Monitoring (DRM) aspects of intelligence. Here’s the deal – at the end of the day there are two main collection areas when it comes to intelligence: Internal and External. For internal TI you are collecting information on what HAS happened and for external you are collecting on what COULD happen. Additionally, for Internal you are monitoring infrastructure that you have direct command and control over, while for external you are collecting for areas that you do not have direct command and control over, but for which you have a “level of presence”.
Digital Risk Monitoring is tied more to the strategic and operational levels of threat intelligence. In current form DRM is typically marketed and tracked as an industry capability separate from cyber threat intelligence, although as the space continues to mature I do believe it is a form of intelligence and thus I have included it in the mind map.
The combination of threat intelligence and digital risk monitoring can help you understand:
• Your most critical areas of risk – from both a security and business risk perspective,
• How malicious actors may try to take advantage of these “opportunities” you’ve presented to them and;
• How best you can minimize or eliminate that risk
Different intelligence consumers in your organization create and consume varying levels of threat intel to take appropriate actions against identified risks. Processes for creating and using the different levels of intel are both for proactive and reactive types of purposes.
In future articles I will be going around this mind map looking at each section in greater detail and how it should be integrated and utilized within your current security program.














