Research-focused security services provider IOActive has conducted an analysis of car vulnerability trends over the past decade and determined that the automotive industry has been placing increasing importance on cybersecurity.
The new IOActive automotive cybersecurity study (PDF) looks at vulnerabilities discovered over the last 10 years, with a focus on trends between 2016, 2018 and 2022.
The company has ranked and grouped vulnerabilities based on their potential real-world impact, their likelihood of exploitation, and their overall risk, with this risk level being calculated based on impact and likelihood.
In terms of impact, the percentage of car vulnerabilities with a critical rating went from 25% of the total in 2016, to 10% in 2018, and 12% in 2022. High-impact flaws gradually decreased from 25% to 21% between 2016 and last year.
However, over the past 10 years, the percentage of critical issues dropped by 13% and high-impact issues by 4%.
In terms of likelihood of exploitation, critical vulnerabilities went from 7% of the total in 2016 to 1% in 2022. High-likelihood issues dropped to 16% in 2022, from 21% in 2016. This, according to IOActive, suggests that vulnerabilities are becoming more difficult to exploit or “the vectors to discover vulnerabilities are becoming less remote”.
“In cybersecurity parlance, there is less ‘low-hanging fruit,’ indicating that between 2018 and 2022, the automotive industry learned from its initial mistakes and is building better,” the cybersecurity firm said.
Overall, the percentage of critical- and high-likelihood vulnerabilities decreased by 6% and 5%, respectively, in the past 10 years.
When it comes to the overall risk, the percentage of high-risk vulnerabilities has increased by 3% and medium-risk issues by 25% in the past 10 years, but critical-risk weaknesses decreased by 17% over the same period.
The ‘critical risk’ rating is assigned to issues that can be exploited remotely and are easy to discover, with impact including complete component compromise or safety concerns. High-risk flaws are ones that can be exploited from nearby or require limited skills, and their impact includes partial component control, sensitive information disclosure or a potential safety concern.
As for attack vectors, physical hardware attacks dropped from 28% in 2016 to 10% in 2022, but local and networked attack vectors have increased. IOActive has also seen a slight but important rise — from 0% to 1% — in radio frequency attacks, particularly remote keyless entry and Bluetooth attacks.
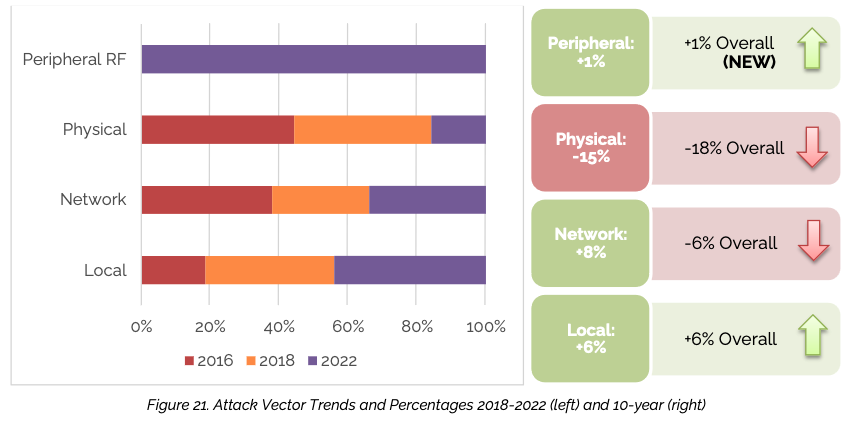
IOActive has attributed the positive trends to the automotive industry building cybersecurity into earlier stages of the development process, as well as its efforts to reduce higher likelihood attack vectors and its improved maturity level in deploying cybersecurity practices.
On the other hand, IOActive has also raised some potential concerns. One of them is that while critical vulnerabilities are less common, threat actors could turn to chaining multiple less severe flaws — such as medium-risk issues, which increased significantly — to achieve their goals, rather than relying on a single critical weakness.
Related: Over $1 Million Offered at New Pwn2Own Automotive Hacking Contest
Related: Automotive Security Threats Are More Critical Than Ever
Related: US Subsidiary of Automotive Hose Maker Nichirin Hit by Ransomware















