Security researchers at ESET have discovered a new piece of Android malware that poses as Flash Player, but instead steals login credentials from roughly 20 mobile banking apps.
Dubbed Android/Spy.Agent.SI, the Android banking Trojan was observed in a campaign targeting customers of large banks in Australia, New Zealand and Turkey and is capable of intercepting SMS communications, meaning that it was designed to bypass SMS-based 2FA (two-factor authentication) systems.
ESET’s Lukas Stefanko explains that the malware was hosted on several domains that were registered early this year, with the URL paths to the malicious APK being regenerated each hour, in an attempt to avoid URL detection. The researcher also notes that the Trojan masquerades as Flash Player and that it has a “legitimate-looking” icon.
 After installation, the app requests admin rights and then hides the Flash Player icon, although the malware remains active in the background. The Trojan communicates to the command and control (C&C) server, sending out information on the device such as model type, IMEI number, language, SDK version, and whether the device administrator is activated.
After installation, the app requests admin rights and then hides the Flash Player icon, although the malware remains active in the background. The Trojan communicates to the command and control (C&C) server, sending out information on the device such as model type, IMEI number, language, SDK version, and whether the device administrator is activated.
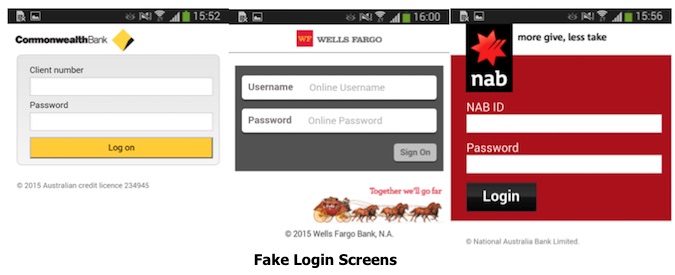
Next, the malware gathers info on installed applications, including mobile banking apps, and sends them to the remote server, which responds with a list of 49 target apps, although only some are directly attacked. The Trojan overlays a window on top of the launched banking application, a phishing activity meant to steal user’s login credentials for mobile banking apps and Google accounts.
The fake login screen that overlays the original banking one is triggered when the application is launched and closes after the user fills their personal data. The information is not verified, but instead it is immediately sent to the server in plain text, although the communication between the device and the server is normally encrypted, Stefanko said.
The Android banking Trojan also captures all received text messages to the server, which allows its operators bypass 2FA mechanisms. All SMS text messages from the bank are immediately redirected to the attacker and removed from the client device, so as not to attract any suspicion.
The mobile banking applications targeted by the malware include those from Westpac, Bendigo Bank, Commonwealth Bank, St. George Bank, National Australia Bank, Bankwest, Me Bank, ANZ Bank, ASB Bank, Bank of New Zealand, Kiwibank, Wells Fargo, Halkbank, Yapı Kredi Bank, VakıfBank, Garanti Bank, Akbank, Finansbank, Türkiye İş Bankası and Ziraat Bankası.
According to ESET, users can uninstall the malware by simply deactivating its device admin rights (Settings > Security > Device administrators > Flash Player) and then simply removing it (Settings > Apps/Application manager > Flash Player > Uninstall).
However, the malware’s operators can also send commands to disable deactivation of device administrator rights, which might complicate things. In such cases, the malware actually creates an overlay activity that presents users with a confirmation button, which, in fact, prevents them from deactivating the admin rights.
Stefanko explains that users can deactivate administrator privileges from Safe mode, since third-party applications are not loaded or executed in this mode. Thus, the user can safely perform the deactivation and then uninstall the malicious application.
Last month, Palo Alto researchers revealed that the Xbot Android Trojan was mimicking the login pages of 7 different banks’ apps, while also capable of locking devices, stealing SMS messages and contact information, and intercepting messages. In January, Symantec security researchers detailed the Bankosy Android malware, which could also deceive voice call-based two-factor authorization (2FA) systems.
















