Industrial cybersecurity firm Dragos has published an analysis of exploits targeting vulnerabilities in industrial control systems (ICS) and operational technology (OT) systems. The company says the findings can help defenders prioritize remediation and mitigation efforts.
Dragos has been tracking more than 3,000 ICS and OT vulnerabilities over the past decade and, unsurprisingly, the disclosure of such flaws has been on an upward trend.
The number of vulnerabilities that came to light in 2020 was lower than in the two previous years. However, more important than the number of vulnerabilities is determining which of them pose a real risk to an organization, and there are several factors that should be taken into consideration when assessing the risks they pose.
Dragos has been tracking not only the disclosure of the vulnerabilities, but also the public availability of the associated exploits, which make it easier for low-skilled threat actors to actually take advantage of the security holes.
The company noted that only 8% of the vulnerabilities disclosed in 2020 have public exploits. One possible explanation is that Trend Micro’s Zero Day Initiative (ZDI) has acquired many ICS vulnerabilities, and ZDI can prevent researchers from making public their proof-of-concept (PoC) exploits.
ZDI acquiring many ICS flaws could also explain why fewer vulnerabilities were disclosed in 2020 — ZDI has a 120-day disclosure policy, which is often extended, making it likely for vulnerabilities found in 2020 to be disclosed only in 2021.
Dragos is aware of nearly 600 public ICS exploits targeting the products of over 110 vendors. However, seven major vendors account for roughly 40% of all published exploits, including Advantech, Rockwell Automation and its Allen-Bradley brand, Moxa, Microsoft, Siemens, and Schneider Electric. Microsoft is included in the list because many ICS/OT systems run on top of Windows and are exposed to attacks due to Windows vulnerabilities.
Many of the public ICS exploits target devices on the “site operations” level, which could serve as an initial access point into the industrial network. A malicious actor has hundreds of publicly available exploits at their disposal once they reach the industrial network, which includes field, control, and supervisory devices.
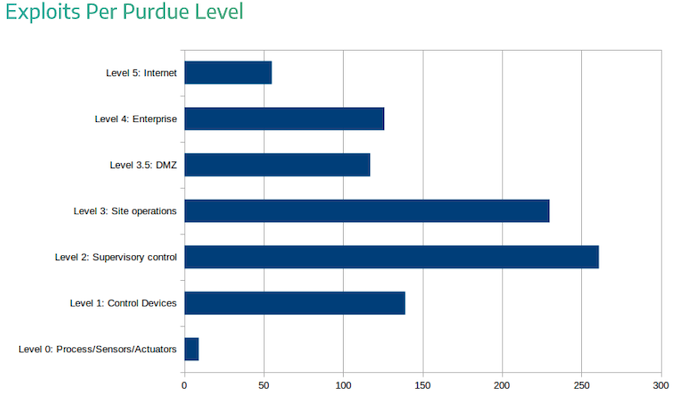
For most levels of access, remote code execution is the most likely impact, but denial of service (DoS) takes the lead in the case of exploits targeting control devices. For controllers and other devices on this level, a DoS exploit can be easier to develop and it could have a bigger impact in a real world environment compared to remote code execution.
Dragos notes that some types of exploits are unlikely to ever be used in real attacks. For example, cross-site request forgery (CSRF) and cross-site scripting (XSS) exploits targeting programmable logic controllers (PLCs).
“For example, a [CSRF] against a PLC is unlikely to ever be used in the wild, because it requires the victim to be logged into the PLC’s web interface and to navigate to a malicious site (or click on a malicious link). It also requires the attacker to be able to craft URLs that address the victim‘s PLC. That is an unlikely scenario,” Dragos explained in its report.
As for who makes the exploits public, Dragos found that in nearly half of cases the exploit author is affiliated with a company or university. The three companies that account for more than half of exploits are Rapid7 (through its Metasploit project), Cisco’s Talos research and intelligence unit, and Tenable.
Roughly one-third of exploits are available in third-party advisories, followed by Metasploit, the Exploit-DB exploit database, personal GitHub or Bitbucket repositories, and various other sources, such as Twitter, whitepapers, bug trackers, Full Disclosure, and Packet Storm.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
In many cases, researchers release PoC exploits when they disclose the vulnerabilities they have found in order to help others gain a better understanding of their work. If these exploits are not taken into account, Dragos has determined that the median time for an exploit to become public after the disclosure of a vulnerability is 24 days.
“ICS/OT network defenders can reasonably expect that, on average, if a CVE is going to get a public exploit, then it will be released within the first 30 days after initial disclosure,” Dragos said.
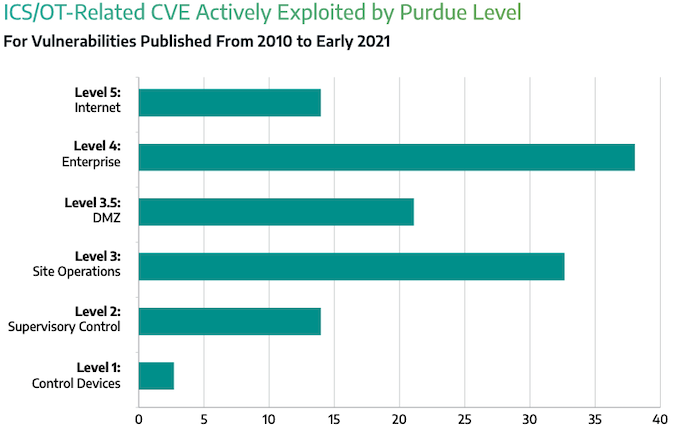
Roughly 10% of the ICS exploits tracked by the cybersecurity firm have been exploited in malicious attacks, and the highest percentages target the enterprise and the site operations levels. Targeting site operations can be profitable for an attacker considering that from this level they could be able to take control of lower-level devices, such as supervisory and control devices, by using legitimate functionality, without the need to exploit vulnerabilities.
Dragos has four main recommendations for defenders looking to prioritize ICS vulnerability remediation. First, they should take into account that exploits are typically made public within 30 days of disclosure, and those that don’t get an exploit within the 30-day window may have lower priority.
The source of the vulnerability is also important since security flaws disclosed by researchers are more likely to have a PoC exploit.
Another recommendation is related to the potential impact of an exploit — if it only affects the OT network and requires user interaction or a man-in-the-middle position, it can be deprioritized.
Finally, vulnerabilities affecting devices on the supervisory and control levels should not be completely ignored as organizations often don’t have good visibility on these levels to know if such exploits are actually being used in malicious attacks.
Related: Many ICS Vulnerability Advisories Contain Errors
Related: Industrial Firms Warned of Risk Posed by Cloud-Based ICS Management Systems












