Researchers at industrial cybersecurity firm Claroty have identified a series of vulnerabilities that have enabled them to demonstrate how malicious actors could abuse cloud-based management platforms when targeting industrial organizations.
Members of Claroty’s Team82 research arm exploited a total of seven vulnerabilities as part of this research, including three affecting CODESYS and four impacting WAGO products. Specifically, the flaws affect CODESYS’s Automation Server platform, which enables organizations to manage industrial control systems (ICS) from the cloud, and some of WAGO’s programmable logic controllers (PLCs).
The researchers showed how an attacker could go from the cloud-based management console to all managed endpoint devices, and also from the endpoint devices to the management console.
The attack scenarios presented by Claroty involve social engineering, exploitation of the WAGO and CODESYS vulnerabilities — these were patched by the vendors in recent months — as well as some other techniques and exploits.
In the first attack, the attacker obtains unauthorized access to the account of a management console operator using stolen credentials or exploits.
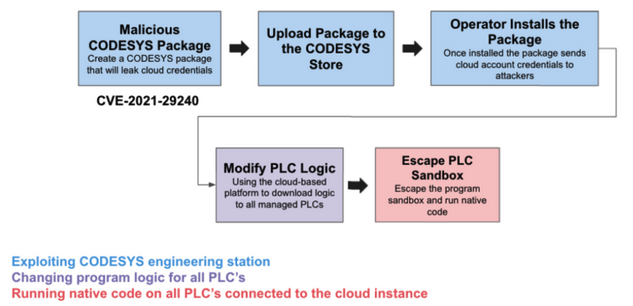
In a theoretical scenario described by Claroty, the attacker creates a malicious CODESYS package designed to leak credentials. These packages, which enable users to add new functionality to CODESYS products, are available on a dedicated application store.
If the attacker manages to upload the malicious package to the CODESYS store and they can convince an OT engineer to install the package, they can execute arbitrary code on the targeted Windows device and obtain the Automation Server credentials.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
“Once attackers gain access to the cloud-based management console, they have a wide attack surface to work with,” Claroty researchers explained in a blog post. “The simplest thing attackers can do is modify or even stop the logic currently running on managed PLCs. For example, an attacker could stop a PLC program responsible for temperature regulation of the production line, or change centrifuge speeds as was the case with Stuxnet. These types of attacks could lead to real-life damage and affect production times and availability.”
An attacker could also try to find exploits that enable them to escape the PLC sandbox, which would allow them to gain complete control of the controller.
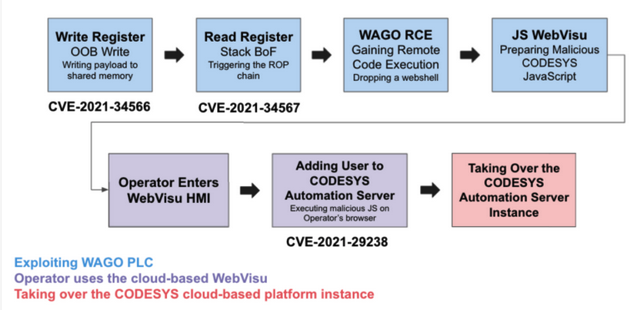
In the second scenario described by Claroty, the attacker goes from a single compromised PLC to the cloud-based management console, from where they can target other managed endpoints.
The researchers showed how an attacker could hijack a WAGO PLC by exploiting an unauthenticated remote code execution vulnerability they discovered, then use the integrated CODESYS WebVisu feature to add a new user to the management platform, and leverage that account to take over the CODESYS Automation Server instance.
Each of these attacks chains the vulnerabilities found by the researchers in WAGO and CODESYS products.
Claroty has provided some high-level recommendations that industrial organizations should follow to minimize the risk of attacks.
Related: Vulnerabilities in OpENer Stack Expose Industrial Devices to Attacks
Related: WAGO Controller Flaws Can Allow Hackers to Disrupt Industrial Processes
Related: Serious Vulnerabilities Found in CODESYS Software Used by Many ICS Products













