The Shadowserver Foundation has seen 45,000 internet-exposed Jenkins instances that appear to be affected by a recently disclosed critical vulnerability, and there are unconfirmed reports of exploitation in the wild.
The developers of the open source CI/CD automation tool recently announced patches for CVE-2024-23897, a critical vulnerability that can allow attackers to read the content of files. Unauthenticated attackers can read limited data from files, while authenticated attackers could read the entire file.
Some files include Jenkins secrets that could enable the attacker to escalate privileges and potentially execute arbitrary code on the targeted server.
Code quality firm Sonar, which discovered the vulnerability, published technical details on January 24 and a proof-of-concept (PoC) exploit was made public a few days later.
Researcher Chaofan Shou, who works at blockchain security firm FuzzLand and is a PhD student at UC Berkeley, reported seeing in-the-wild exploitation on January 25, even before the PoC exploit was published.
“We host hundreds of honeypots across the globe and we have sniffed connections conducting the CVE-2024-23897 attacks against Jenkins instances supporting anonymous access since 1/25. We have confirmed the in-the-wild exploitation and extracted the exploit from the attack,” the researcher told SecurityWeek.
“We observed attacks with different patterns from different sources. The first and most notable one attempted to first read Jenkins secret key files and ssh keys, then dump Jenkins credential files,” he added.
No one else appears to have confirmed in-the-wild exploitation. Threat intelligence firm GreyNoise, which tracks vulnerability exploitation attempts, told SecurityWeek that it currently does not have any insights for CVE-2024-23897, but the company did recently see a ‘single ping’ targeting an old Jenkins vulnerability disclosed in 2015.
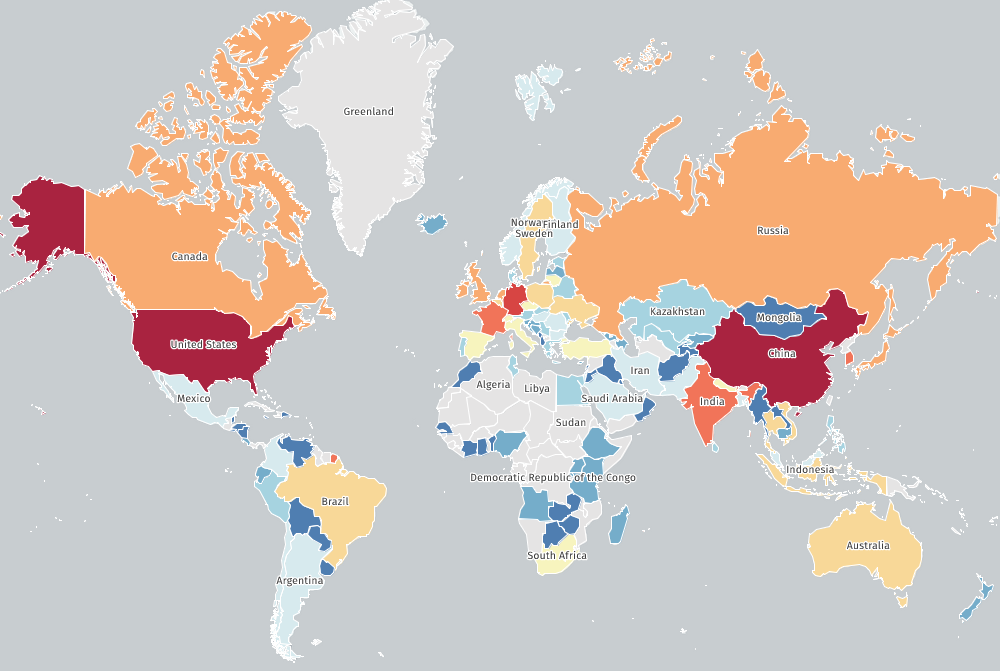
Of the 45,000 internet-exposed instances seen by Shadowserver, a majority are located in the United States and China, with roughly 11,000 systems each, followed by Germany, India and France.
Related: Vulnerabilities in WatchGuard, Panda Security Products Lead to Code Execution
Related: Cisco Patches Critical Vulnerability in Enterprise Collaboration Products
Related: PoC Code Published for Just-Disclosed Fortra GoAnywhere Vulnerability














