Some Sierra Wireless cellular routers are affected by 21 vulnerabilities, including ones that could pose a significant risk to impacted organizations, including in critical infrastructure sectors, according to network security and risk management company Forescout.
The vulnerabilities, collectively tracked as ‘Sierra:21’, were found by Forescout researchers in Sierra Wireless AirLink OT/IoT routers that are often used to connect local networks to the web in sectors such as healthcare, manufacturing, government, energy, water, transportation, emergency services, and retail.
Of the 21 vulnerabilities, one has been assigned a ‘critical severity’ rating and nine are ‘high severity’. They include remote code execution, unauthorized access, authentication bypass, denial-of-service (DoS), and cross-site scripting (XSS) flaws.
Forescout said some of them can be exploited to steal credentials and take control of a router by injecting malicious code. An attacker can gain persistent access to a targeted device and use it as an entry point into a critical network. This makes the flaws useful for various types of attacks, including for espionage and causing disruption.
The company has described theoretical attack scenarios where hackers exploit these vulnerabilities to compromise patient and staff devices in a healthcare facility, as well as industrial control systems (ICS) in a manufacturing plant.
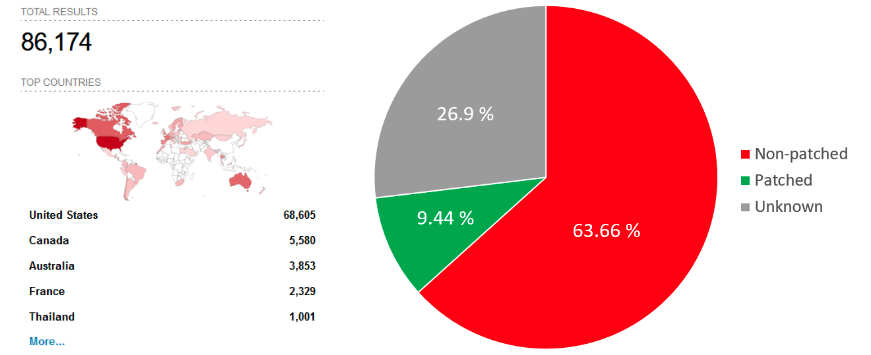
Worryingly, the cybersecurity firm found 86,000 vulnerable routers that are directly exposed to the internet. Only less than 10% of them appear to be patched against known vulnerabilities disclosed since 2019, and many exposed devices have reached end of life and no longer receive patches.
Eight of the identified vulnerabilities are specific to the ALEOS operating system shipped with certain AirLink routers, including MP70, RV50x, RV55, LX40, LX60 ES450 and GX450. The Canadian wireless communications equipment maker published an advisory on November 28 to inform customers about these vulnerabilities and the availability of patches.
The security holes impact ALEOS 4.16 and earlier versions, and have been patched in ALEOS 4.17, released in October 2023. It’s also worth noting that the vendor recommends against exposing devices directly to the internet.
The remaining flaws found by Forescout impact the OpenNDS open source captive portal engine, which is used by other vendors as well.
Forescout told SecurityWeek that it took Sierra Wireless 128-133 days to release patches. The company compared this to the OT:Icefall vulnerabilities it disclosed last year, where the average time to patch was 178 days from initial notification, and the Project Memoria vulnerabilities, for which patches were released 100 days after public disclosure.
Related: InHand Industrial Router Vulnerabilities Expose Internal OT Networks to Attacks
Related: Unpatched Vulnerabilities Expose Yifan Industrial Routers to Attacks
















