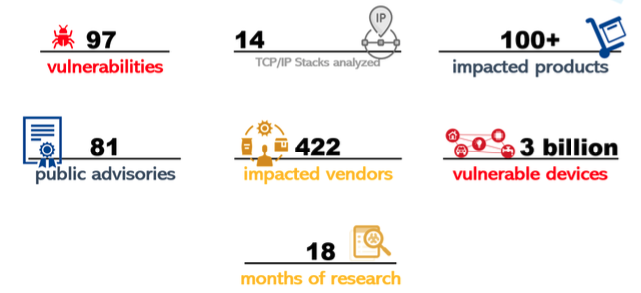
An 18-month research project has resulted in the discovery of nearly 100 vulnerabilities across more than a dozen TCP/IP stacks.
The research, named Project Memoria, was conducted by enterprise device security firm Forescout in collaboration with others. It resulted in the discovery of the vulnerabilities tracked as Ripple20, AMNESIA:33, NUMBER:JACK, NAME:WRECK, INFRA:HALT, and NUCLEUS:13.
TCP/IP stacks are leveraged by a wide range of devices for communication, including medical products, industrial control systems (ICS), printers, and switches.
Researchers have identified a total of 97 vulnerabilities across 14 TCP/IP stacks, including ones that can be exploited for remote code execution, DoS attacks, or to obtain sensitive information. The flaws impact hundreds of products, with researchers estimating that there are roughly 3 billion vulnerable devices.
Project Memoria targeted a total of 15 TCP/IP stacks, including CycloneTCP, FNET, FreeBSD, IPnet, lwIP, MPLAB Net, NetX, NicheStack, NDKTCPIP, Nucleus NET, Nut/Net, picoTCP, Treck, uC/TCP-IP, and uIP. In only one of them, lwIP, researchers haven’t found any vulnerabilities.
Some of these TCP/IP stacks have been around for nearly 30 years, but they are still actively developed. While their developers continue to release patches for vulnerabilities, those patches often don’t make it to end user devices, in large part due to what researchers describe as “silent patching.” Silent patching refers to some developers fixing vulnerabilities without assigning CVE identifiers, which results in device vendors and their customers not knowing about the flaws.
“[Silently patched vulnerabilities] exist in very critical supply-chain software, so there are millions of devices out there that have been vulnerable for a long time without even their vendors knowing about it because other vendors chose to remain silent,” Forescout said in a report summarizing Project Memoria. “Silently patching a vulnerability does not mean that nobody will get to know about it: these issues tend to be rediscovered again and again.”
While silent patching can be problematic, some vendors don’t respond or fail to take action when notified about vulnerabilities. Forescout has identified 422 device vendors whose products could be vulnerable. However, only 81 of them have issued advisories and of the 36 that have confirmed being impacted 10 said they will not provide patches.
“This means that only 19% of potentially affected vendors have provided some public response and only 5.5% have actually patched the vulnerabilities,” Forescout said.
An analysis of a quarter of a million devices affected by the Project Memoria vulnerabilities showed that the highest number of vulnerable systems are housed by the government and healthcare sectors, followed by manufacturing, retail, and financial.
The most common types of vulnerable devices are printers, VoIP products, industrial controllers, storage systems, and networking devices. In the case of healthcare organizations, infusion pumps and building automation systems are often impacted.
“The main conclusion of Project Memoria is that supply-chain vulnerabilities are here to stay but mitigation is possible, as long as both the security community and individual organizations take action,” Forescout concluded.
Related: Many Healthcare, OT Systems Exposed to Attacks by NUCLEUS:13 Vulnerabilities
Related: At Least 100M Devices Affected by “NAME:WRECK” DNS Flaws in TCP/IP Stacks














