As a defender, your mission is to reduce the impact of cyber threats to your organization. A good day means that the organization was not impacted by a cyber event.
Thinking about this reminds me of my early days serving in the Navy on Force Protection missions. Many moons and about 60 pounds ago I was a part of a small boat unit conducting force protection, intelligence and boarding operations. Basically we were always on the lookout for bad guys doing bad things and shadowing the good guys doing good things to make sure everything stayed “calm and quiet”.
And for us “calm and quiet” = Mission Success.
In the cyber world, it’s not much different. Cybersecurity professionals are on the lookout for bad guys doing bad things and making sure the good guys have the freedom of movement to do good guy things.
In a geographically hostile environment, you have already taken on the exposure of a high risk area where threats are highly likely. Operating in a hostile environment enables pretty clear justification for applying more security resources to protect assets in this region. To reduce malicious intent, simply remove yourself from the geographical area and operate from a safer location.
However in the digital world, especially in the private sector, it’s not as clear cut. You see, when you are operating in an area without borders, you don’t get to dictate where to position yourself – there is no “safe zone” on the internet. In order to conduct business you have to expose yourself to an environment without borders and many organizations are not prepared to size up an adversary.
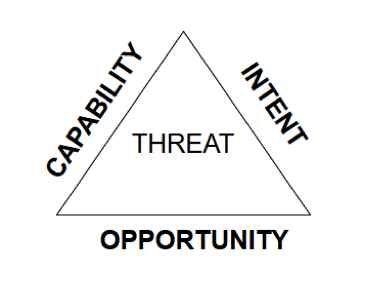 One of the tools I used when sizing up a situation was to leverage the “Threat Triangle”. The Threat Triangle is similar to rules of engagement. My rules of engagement at the time dictated that I could not engage any threat unless they displayed the Capability, the Opportunity and the Intent to cause harm.
One of the tools I used when sizing up a situation was to leverage the “Threat Triangle”. The Threat Triangle is similar to rules of engagement. My rules of engagement at the time dictated that I could not engage any threat unless they displayed the Capability, the Opportunity and the Intent to cause harm.
Nowadays, when conducting intelligence work I use this same method. Does the Actor have the capability to cause an event? Have they been known to do it in the past? Have they followed through on a past threat? Are there indicators that give evidence that the actor has operated in the space previously? Do they demonstrate intent? Are they active in communications forums? Do they actively buy/sell/trade commodities? The answers to questions such as these will give you a level of capability and intent.
Out of those three aspects you generally have no control over Capability and Intent, but you can influence the third (Opportunity) to affect change.
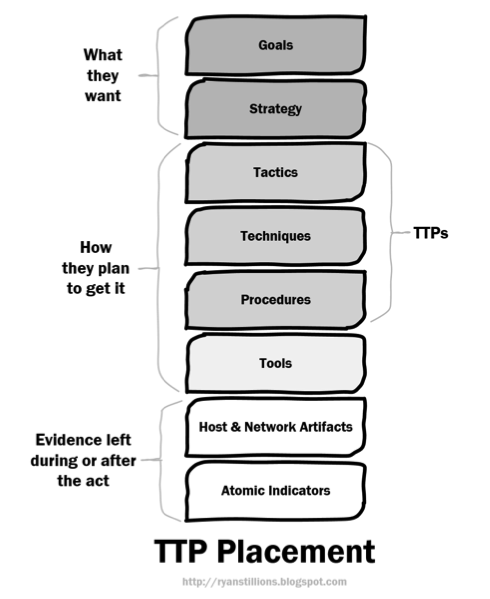 A very wise person by the name of Ryan Stillions, (I recommend you check his blog out for more good stuff) created a TTP stack outlining three core areas:
A very wise person by the name of Ryan Stillions, (I recommend you check his blog out for more good stuff) created a TTP stack outlining three core areas:
1. What an adversary wants
2. How they plan to get it
3. The evidence left behind after the event occurs
This diagram represents very well the “flow” of events as an adversary establishes a level of presence within a target and follows through on their desires. It does a good job of reflecting the intent (Goals and Strategy) and the capability (TTP) areas.
However, what’s missing from this representation is that it does not represent the adversary’s opportunity – essentially what are the openings (targets of opportunity) an organization is presenting that an actor can then exploit.
To achieve the Threat Triangle aspect, I modified the original diagram to reflect capability, opportunity and intent.
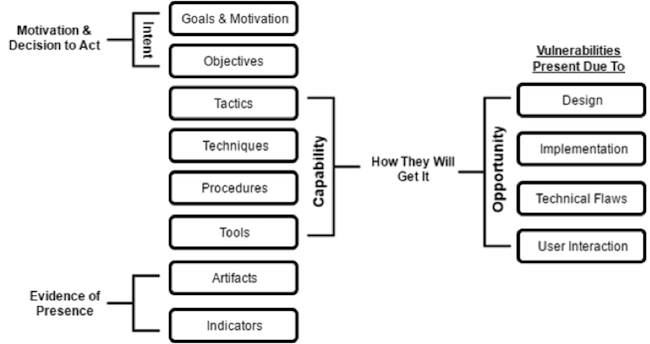
As you can see, the root issue here is that our adversaries require “us” to present vulnerabilities to them in order for them to succeed. If you remove the opportunity you are directly influencing their capability within the Threat Triangle.
You will notice in the opportunity area on the right hand side I labeled it “Vulnerabilities Present Due To” this is not an exhaustive list, but meant to highlight that “we”, “you”, “us” open up opportunity for the actor to leverage their capability and intent. We are vulnerable because we deploy vulnerable systems.
In addition to supporting defenders in identifying when a set of TTP’s are being utilized for detection and response efforts, a core threat intelligence requirement should also place a spotlight on which “opportunities” are being leveraged by adversaries when they conduct their efforts.
That is basically what me and my team were doing when I was operating overseas – we were removing the opportunity for the bad guys to do bad things either directly or indirectly.
That is what cyber threat intelligence, if done right, can do as well – remove cyber actors’ opportunities, rendering their capability less capable and their intent harder to pull off.
Look at breach history in various sectors and look at your own internal incident information. How much was due to organizations opening the door and giving the adversary the opportunity? How much of it was due poor maintenance, poor oversight, and/or poor cyber hygiene? I think you know the answer. You control how much opportunity you give and good cyber threat intelligence can support that analysis.

















