The Qualys 2023 TruRisk Research Report discusses the five most exploited vulnerabilities of calendar year 2022, and the five key ‘Risk Facts’ that security teams need to consider.
To compile the report, the Qualys Threat Research Unit analyzed more than 13 billion events to gain insight into the vulnerabilities found on devices, the security of web apps, and the misconfiguration of on-premise devices.
The most exploited vulnerabilities are CVE-2022-30190 (Follina); CVE-2022-26134 (Atlassian); CVE-2022-22954 (VMware); CVE-2022-1040 (Sophos Firewall); and CVE-2022-24521 (Windows). The first four all have a Qualys vulnerability score (QVS) of 100; the last scores 95. All five have been used in ransomware attacks, and all five are included within CISA’s KEV list.
CVE-2022-30190, Follina, leverages Microsoft URL handlers ultimately allowing PowerShell commands to provide remote code execution. It is known to have been used by at least four named threat actors, including Fancy Bear, Wizard Spider, Luckycat and UAC-0098. Qualys knows of six malwares that have used the vulnerability, including the Qakbot, Skeeyah, and Black Basta ransomwares. The patch rate for this vulnerability is relatively high at 91.21% taking an average of 28.4 days from the patch release – but this was from a total of 12.8 million world-wide detections, so the number of unpatched devices remains high.
CVE-2022-26134, Atlassian, unauthenticated remote code execution allows an attacker to execute arbitrary code on a Confluence Server or data center instance. It has been exploited by at least four malware families including Sparkling Goblin and the two ransomware groups Cerber and AvosLocker. Despite ease of execution, its patch rate is low at 58.30% taking an average of 28.5 days.
CVE-2022-22954, VMware, is a remote code exploitation vulnerability that can be easily exploited by anyone with access to a vulnerable instance. It was one of five weaponized vulnerabilities discovered at the time; two of which were added to the KEV list, but only one (this one) leveraged by threat actors and ransomware groups. Qualys specifically mentions the Rocket Kitten group, and the RAR1Ransom and Clop ransomware families. It has an 87.3% patch rate at an average of 14.3 days.
CVE-2022-1040i, Sophos, is a firewall authentication bypass vulnerability that allows unauthorized access to the firewall to execute arbitrary code. It has been used by the LuckyCat and DriftingCloud, threat groups and used by the Ragnarok ransomware family. It has a patch rate of just 34.7% taking an average of 70 days.
CVE-2022-24521, Windows, is a vulnerability affecting the CLFS driver. It allows privilege escalation and would be used in conjunction with other exploit techniques. Such vulnerabilities are typically used after an attacker has gained access to the vulnerable system to elevate privileges. It was detected in more than 14 million instances. CISA added it to the KEV list two days before the NVD published the CVE. It is known to have been used by UNC2596 and Vice Society, while other exploits have been observed from four malware families, including N13V/RedAlert, Cuba, and Yunluowang. It has a 90% patch rate at an average of 20.6 days.
From its analysis, the Qualys team has isolated five key risk facts that security teams should consider. These are the need for speed in vulnerability triaging; the need for automation in remediation; a need to be cognizant of initial access brokers; a need to avoid misconfigurations in web apps; and awareness that infrastructure misconfigurations open the door to ransomware.
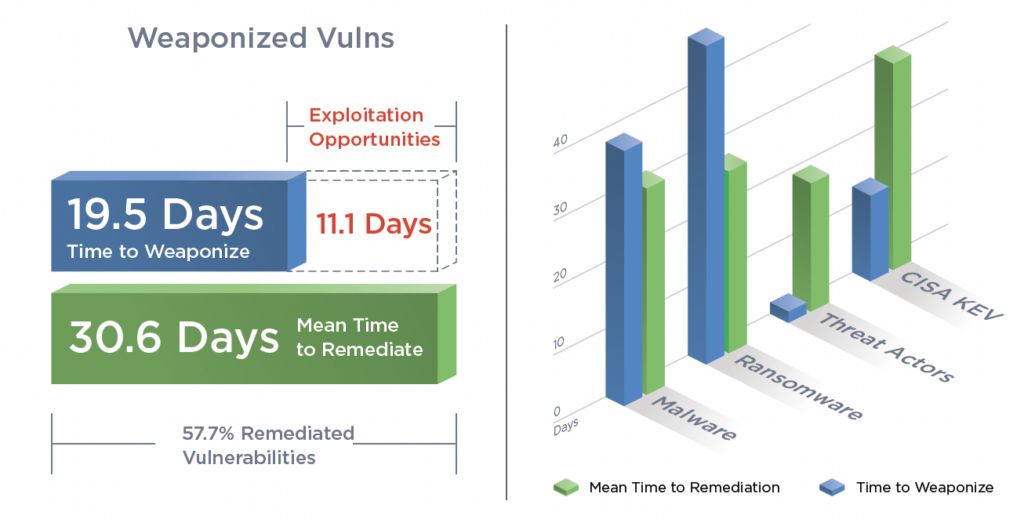
For remediation, attackers take just under 20 days to weaponize a vulnerability, while defenders take a little over 30 days to patch. This leaves a period of 11 days average exploitation period for the attackers. The sheer volume of vulnerabilities and the defenders’ lack of resources means that prioritizing on the most important risks is essential. “Security teams need a systematic approach to cut through the noise and prioritize fixing the most critical vulnerabilities that will reduce risk and enable them to keep up with threat actors.,” says the report (PDF).
Automation is the best and essential way to achieve this. “It allows organizations to eliminate manual and tedious tasks, which ultimately reduces the time and effort it takes to remediate vulnerabilities,” says Qualys, “and frees up security staff to address more pressing concerns.”
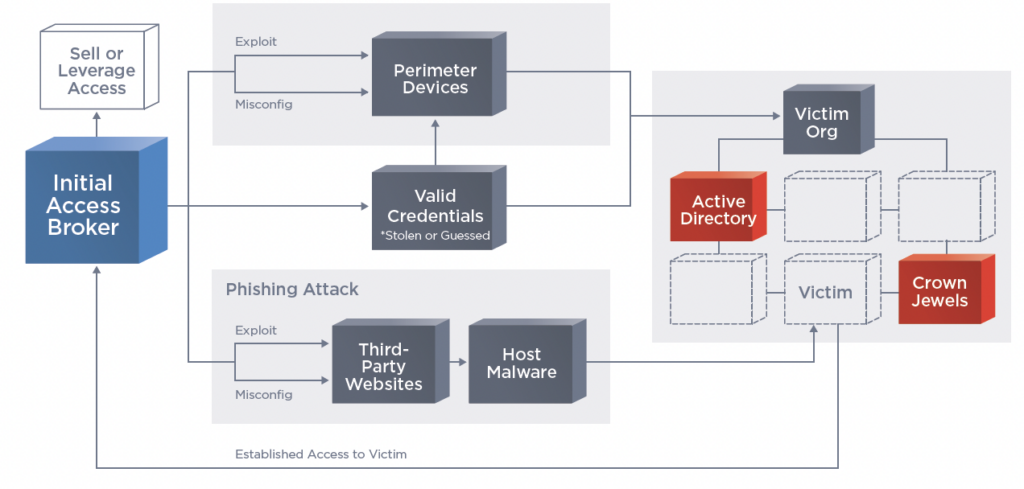
The activity of the initial access broker (IAB) is rising and needs to be considered. There are two primary routes: either to exploit the perimeter devices of the target, or to leverage valid credentials (which can be either stolen or purchased on the dark web).
Since the IABs don’t primarily or immediately make use of the access acquired, the breach may initially be missed by the defense team. The IAB’s purpose is to sell the access to other attackers, either for a flat fee or a percentage of revenue (particularly if that access is subsequently used successfully by a ransomware group. “During 2022, there were 17 new CVEs added to the IAB toolkit,” notes the report.
The fourth and fifth risks both apply to misconfigurations. For the fourth risk, Qualys notes that they are still prevalent in web apps. Qualys scanned 370,000 web apps and found 25 million vulnerabilities. A massive 33% of these were down to misconfigurations. Two notable misconfiguration types occur through inadequate use of best practices: either a failure to change default permissions or passwords, and/or allowing the app to share too much information.
The second type of misconfiguration – the fifth risk – relates to infrastructure. These misconfigurations, says Qualys, open the door to ransomware. “Data exfiltration due to misconfiguration in S3 buckets is a serious concern as it can result in high-profile security breaches,” says the report, adding that individual files within buckets must also be protected. “Unfortunately, only 40% of organizations are currently utilizing preventative controls to prevent files from being accessed publicly.”
The link between misconfigurations and ransomware is most easily seen in the failure to adequately configure RDP access. RDP has long been a primary access route for ransomware attackers to gain entry. Further misconfigurations within the infrastructure allow lateral movement.
Qualys recommends focusing defense on these five risks: use a threat-informed defensive strategy to triage vulnerability remediations; use automation for patching; be wary of externally facing systems that can be exploited by initial access brokers; scan all web apps for vulnerabilities and configuration issues; and understand the ‘shared responsibility’ concept of cloud usage while employing the CIS Hardening Benchmarks to protect cloud workloads.
Related: Cisco Patches High-Severity Vulnerabilities in IOS Software
Related: Exploitation of 55 Zero-Day Vulnerabilities Came to Light in 2022: Mandiant
Related: Cyber Insights 2023 | Ransomware
Related: Cyber Insights 2023 | Criminal Gangs