Kaspersky Lab’s recently launched ICS-CERT department has published a report detailing the industrial sector threat landscape based on data collected by the company in the second half of 2016.
According to the security firm, its products have blocked attack attempts against more than 39 percent of protected industrial systems running Windows. This includes SCADA systems, data storage servers (i.e. historian), data gateways, engineer and operator workstations, and human-machine interfaces (HMI).
On average, the company detected attacks against roughly 20 percent of industrial computers every month in the second half of 2016. These devices were mainly attacked via the Internet (22%), removable media (11%) and email (8%).
Learn More at the 2017 Singapore ICS Cyber Security Conference
Kaspersky pointed out that while stationary workstations on the operational network (OT) don’t typically have an always-on Internet connection, the devices used by network administrators, developers and contractors can often freely connect to the Internet, and experts believe these machines are the most exposed.
In the case of email attacks, hackers leveraged common topics (e.g. banking, package delivery messages) to send malware hidden in VBS, JavaScript, Word, NSIS, AutoCAD, HTML, Java, BAT, PDF and Excel files.
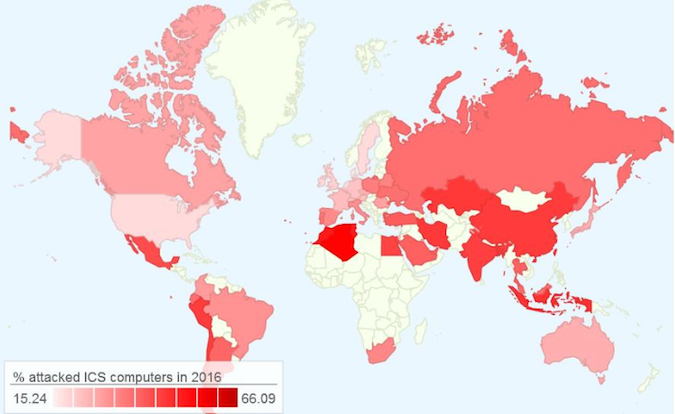
The most targeted countries, relative to the total number of ICS they host, are Vietnam, Algeria, Morocco, Tunisia, Indonesia, Bangladesh, Kazakhstan, Iran, China, Peru, Chile, India, Egypt, Mexico and Turkey. The United States and Western European countries are far less targeted, according to Kaspersky data.
Kaspersky warned that targeted attacks aimed at organizations in industrial sectors are increasingly common. These campaigns involve both widely available malware and custom threats, including zero-day exploits.
One of the spear phishing campaigns observed by the security firm targeted more than 500 companies in over 50 countries worldwide. The attack, which is still ongoing, has mainly targeted industrial companies in sectors such as metallurgical, electric, construction and engineering.
The operation relied on social engineering emails sent from corporate mail servers previously infected with spyware designed to steal account credentials. The delivered malware was common, but the samples had been packed using VB and MSIL packers modified specifically for this attack.
As for non-targeted attacks, Kaspersky identified roughly 20,000 malware variants across more than 2,000 families on industrial systems. While many of these threats are Trojans, researchers also spotted worms, viruses, exploits and ransomware.
“Remarkably, there is very little difference between the rankings of malware detected on industrial computers and those of malware detected on corporate computers. We believe that this demonstrates the absence of significant differences between computers on corporate networks and those on industrial networks in terms of the risk of chance infections. However, it is obvious that even a chance infection on an industrial network can lead to dangerous consequences,” Kaspersky said in its report.
Kaspersky experts have identified a significant number of vulnerabilities in ICS products in the past months. Last year, they reported finding 75 flaws, including 58 rated highly critical. Only 30 of these security holes have been addressed as of March 2017.
Kaspersky Lab will be hosting its annual Security Analyst Summit (SAS) next week in St. Maarten. The company will aslo be presenting an overview of the industrial sector threat landscape at SecurityWeek’s 2017 Singapore ICS Cyber Security Conference next month.
Related: Non-Targeted Malware Hits 3,000 Industrial Sites a Year
Related: Exploring Risks of IT Network Breaches to Industrial Control Systems














