Many industrial and critical infrastructure systems are connected to the Internet, and the operational technology (OT) networks of some organizations have already been compromised, according to a new study from industrial security firm CyberX.
What makes the CyberX study interesting is the fact that it’s not based on a survey. Instead, the company used data obtained after passively monitoring traffic from 375 OT networks over the past 18 months. The organizations whose networks have been analyzed are from a variety of sectors – including manufacturing, energy and utilities, oil and gas, and pharmaceuticals and chemicals – in the United States, Europe and the Asia-Pacific region.
Organizations have often downplayed the risks associated with the presence of vulnerable industrial control systems (ICS) on their networks, claiming that devices are isolated, or air-gapped, and cannot be accessed remotely from the Internet.
However, CyberX’s study revealed that roughly one-third of organizations had industrial networks connected to the public Web. These systems are often accessible remotely for convenience, including for remote management, performing software updates, and even web browsing and email from the OT network.
More than 80% of industrial sites are running a remote management protocol such as RDP, VNC or SSH, allowing attackers on the OT network to remotely access and control other devices on the network via standard administration tools. Misconfigured wireless access points (WAPs) can also be leveraged as an attack vector, and one in five of the analyzed companies had at least one WAP.
CyberX also found that 76% of analyzed industrial sites have machines running obsolete versions of Windows, such as Windows 2000 and Windows XP, on their OT networks. Both Windows devices and industrial systems such as programmable logic controllers (PLCs) had vulnerabilities in 28% of cases.
Furthermore, many organizations haven’t made sure that strong authentication mechanisms are in place. In nearly 60% of cases, CyberX has seen plaintext passwords crossing the network, allowing man-in-the-middle (MitM) attackers to obtain valuable information.
The analysis shows that Modbus is the most widely used industrial protocol (58%), followed by Ethernet IP (28%), Siemens’ S7, OPC, OSIsoft PI and MMS.
Researchers also found that almost half of industrial sites did not have even basic antivirus protection on Windows endpoints.
“We’ve heard from customers that adding AV software to endpoints such as HMI workstations can sometimes void the warranty provided by their OT vendors. Vendors are concerned that the overhead of AV scanning software will impact the performance or reliability of their workstations,” CyberX said in its report. “Nevertheless, lack of AV protection increases the risk of having known malware on these systems — such as Conficker, WannaCry, and NotPetya — without even knowing about it.”
As a matter of fact, CyberX did see malware in 10% of the analyzed OT networks. The security firm has observed Conficker infections, which is one of the most widespread pieces of malware and it has been known to infect even critical infrastructure organizations. CyberX told SecurityWeek that it also noticed some threats that exhibited behavior consistent with the EternalBlue exploit, which has been used by both the WannaCry ransomware and the NotPetya wiper.
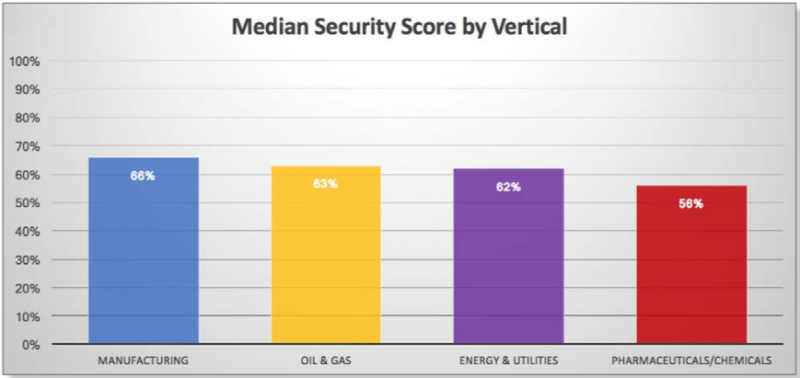
The data shows little difference between the security scores of various industries – there is only a +/- 5% variation from the median score of 61% across the analyzed sectors.
Related: Average Patching Time for SCADA Flaws Is 150 Days













