Industrial cybersecurity and threat intelligence firm CyberX announced on Thursday the availability of a new simulation technology that allows organizations to predict breach and attack vectors on their networks.
The new industrial control systems (ICS) security service, named ICS Attack Vector Prediction, leverages proprietary analytics to continuously predict possible attack avenues and help organizations prevent breaches.
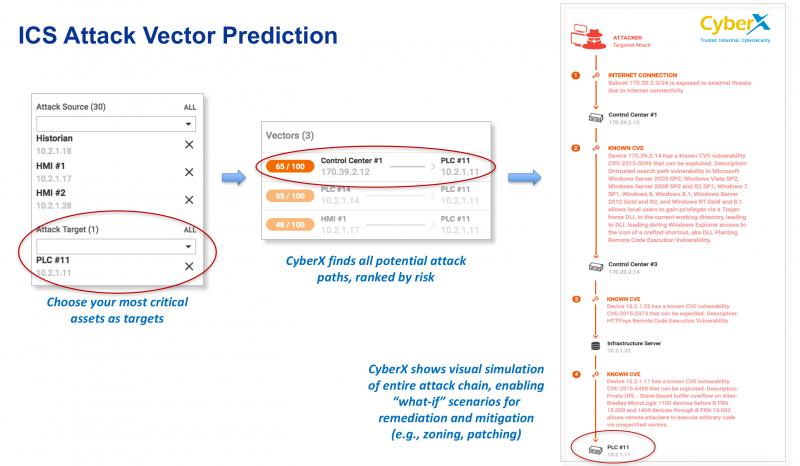
The solution provides a visual representation of all possible attack chains targeting critical assets in the operational technology (OT) network. Scenarios are ranked based on the level of risk to help security teams prioritize mitigation.
Cybersecurity personnel are provided detailed mitigation recommendations for each vulnerability. This can include patching Windows devices, upgrading vulnerable PLC firmware, and disabling unnecessary or unmanaged remote access methods.
CyberX’s in-house ICS security experts can also advise organizations on how to devise the most efficient and effective mitigation strategies, especially in large and globally-distributed organizations in sectors such as manufacturing, pharmaceuticals, chemicals, and oil and gas.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
Security teams can easily simulate the effects of each mitigation action. For example, they can simulate patching or isolating a device in order to determine if that eliminates the risk posed to important systems.
Scanning OT networks is not as easy as scanning IT networks because invasive actions can cause downtime. In order to prevent disruption to the customer’s systems, CyberX says its product simulates attack vectors by using agentless asset discovery and vulnerability assessment technology that combines a deep understanding of industrial systems and non-invasive traffic analysis.
The Attack Vector Prediction technology is available now as part of the base CyberX platform at no additional charge to existing customers. The CyberX platform is priced based on the number of monitored appliances, both physical or virtual.
With the addition of the attack prediction technology to its offering, CyberX says it addresses all four requirements outlined in Gartner’s Adaptive Security Architecture framework: prediction, prevention, detection and response.
Related: CyberX Launches Industrial Threat Intelligence Initiative
Related: Industrial Cybersecurity Firm CyberX Raises $9 Million