IoT Devices are Dramatically Expanding Your Digital Footprint IoT devices are the rage for consumers and business alike. While sound business has always been data-driven, consumers have latched onto data and remote control capabilities. IoT devices are convenient, giving us access and availability to things previously not possible unless you were physically in front of the device. They also can produce useful data for us to process and use to make better decisions.
IoT devices are giving me a sense of Déjà vu… like I have had to deal with this before … a few times.
Circa 2000-2005 when Virtual Machines started to become the go-to technology of the time, many a CIO was raising their fist in victory by consolidating physical hardware into a virtualized environment and claiming cost savings. Only the cost savings were negligible or non-existent when you factored in the massive expansion of the digital footprint that now had to be secured and managed.
Fast forward to the 2009’ish timeframe and a magical term called BYOD started to show up. “Hey look!” said the CIO, “we can let people use their own devices and save on our hardware costs”. Except now we are explicitly co-mingling data that needs to be protected with personal devices. Ever had to do e-discovery on a BYOD device? Fun times. I was a CISO when this BYOD trend hit the street and instead of jumping at the bit to be a first-adopter, I took a wait and see approach. I’ve lost count of how many horror stories I heard about early day BYOD adoption problems.
Just like VM’s and BYOD/Mobile, IoT devices can also create a major risk for organizations – by dramatically expanding their level of presence. All of these devices create more opportunities for cybercriminals to exploit. And I’ve read many reports projecting the number of “smart” devices to double or triple within the next four years. Most of these devices are consumer-based, lack basic cybersecurity features and are not under centralized management. Just look around your office and what do you see?
In this pie chart, my threat intelligence analyst team at SurfWatch Labs has looked at the threat data over the last year and aggregated all of the targeted IoT devices to put some more color to this risk. Needless to say, there are a lot of new avenues for cybercriminals to exploit to gain unauthorized access to more important systems and information.
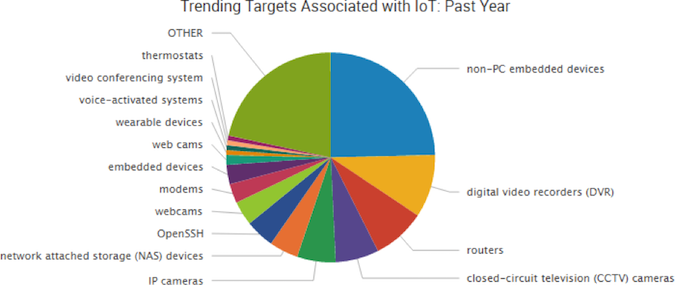
Not only are there more devices expanding your digital footprint, business and personal devices, apps and data are being co-mingled more than ever. What this all adds up to is potentially the largest digital footprint that is NOT under proper security management.
Cybercriminals recognize this!
When looking at the threat landscape and bad actors, the value of good cyber threat intelligence is that it can help provide critical insights on cybercriminals’ motivations and intent, capability and opportunity. What organizations can control is the opportunity presented to the bad guys. And right now there is huge opportunity to cause harm via IoT devices, which is why I wrote that we will see more increasingly creative IoT attacks in the coming year. This forecast was based on the expanding deployment and use of IoT devices, the ability of cybercriminals to turn these devices into powerful botnets as proven in the second half of 2016 with Mirai, and the “as-a-service” capabilities that have been observed on the Dark Web.
The latest IoT-related threat to emerge in 2017 is Imeij, which has been detected in the wild targeting equipment made by Taiwanese manufacturer AVTech. Proof of concepts are also occurring with researchers highlighting how PLC controllers can be hacked and potentially taint water supply.
The reality is that IoT devices will continue to grow and be used by more individuals and businesses. The challenge is to account for these devices in your overall security and risk management process. Here are some recommendations to get visibility and some management around these devices:
1. Get your policy in place. At the end of the day, it all starts with policy. This first step an organization needs to undertake is to define what IoT is and how it should be utilized within the organization via a policy that everyone can reference. How does the organization define IoT? How does it communicate lines of accountability? What are the rules of the road and acceptable uses for both organizationally operated IoT as well as employee owned and operated IoT? A lot of us went through these similar growing pains when BYOD/Mobile devices became the norm, requiring time for the organization to properly adapt. With regards to IoT devices, the same approach makes sense here – hopefully with lessons learned from BYOD/Mobile efforts.
2. Designate clear ownership and accountability. For example, IoT devices intersect physical and logical security, so who in your organization owns this risk? Who is accountable? Just like other aspects of technology there is a need for a shared accountability between the stakeholder (user representative) and the team that supports Information Technology such as the CIO organization. To put this into real terms, a smart light bulb that is network-enabled is not just a light bulb, but rather an IT device that produces light – and as such, it can’t be treated like a regular facilities consumable.
3. Segment your network. The trusted cybersecurity best practice of network segmentation applies to IoT device risk. A smart light bulb that is connected to your network needs to be accounted for in your zoning architecture. Devices designated as IoT should live in their own zone and not be co-mingled with other traditional IT devices. As cybercriminals look for new and easy paths to gain unauthorized access to your sensitive data and systems, beyond the first step of blocking these threats, make sure that if they get past your line of defense, their freedom of movement is severely restricted to minimize the harm that can be done.
4. Information Technology Governance. In relation to item #1 above, IoT devices should be put through an IT Governance process before they can be placed into production – and that starts with procurement. Continuing the smart light bulb example, as devices move beyond analog and into the digital realm and ultimately become an IoT enabled device, contracting and procurement processes need to be updated to reflect this change. A smart light bulb should go through an IT procurement process rather than a facilities “office supplies” process.
To be clear, I think IoT devices provide many productivity and information benefits. I’m for them. But, as with anything new, you need to prepare and plan for these devices being in your environment to maximize the value they provide, while minimizing the inherent risk of these network-enabled devices. By following the four steps above you can get a good start on safely benefitting from IoT devices, along with continuing to have intel on relevant threat campaigns a
nd actors targeting these devices.














