Charles Schwab Clients Targeted in Recent Malware Attack
Threat researchers from Fortinet have decrypted a yet another variant of the Zeus botnet, one that specifically targets Charles Schwab customers.
Fortinet researchers have verified that the variant is sending stolen credentials to the command and control host, which currently uses 6 domains, 5 of which point to a single server in Great Britain and 6th domain hosted on “fast flux” IPs worldwide, according to Fortinet. “Fast Flux DNS” is a common method that botnets use to hide their phishing and malware distribution sites. With fast flux DNS, the malicious sites hide behind many different hosts serving as proxies, utilizing numerous IP addresses associated with a domain name by rapidly changing the IP addresses as a result of frequently modifying DNS records.
Fortinet notes that this attack uses an enhanced, more rigid encryption scheme and a very specific injection payload – capable of causing a big impact.
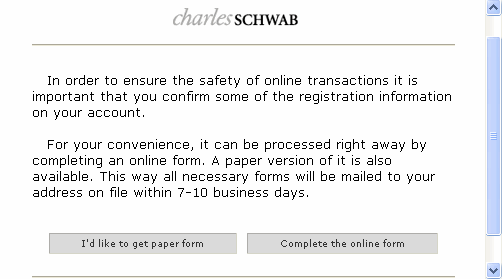
Built using the newer Zeus 2.0 toolkit, this variant contains updated encryption, and a slightly modified configuration file to evade detection from existing tools that decrypt Zeus v2.0 config files.
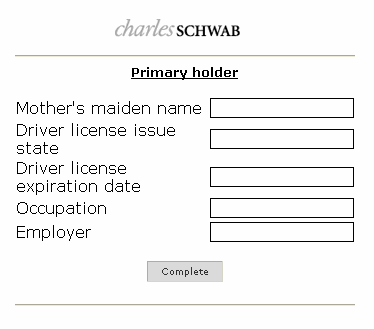
Kyle Yang of Fortinet decrypted the latest configuration file and was able to disover the intentions and targets for this ZBot attack: banks and investment accounts. With this attack, cybercriminals have expanded their scope, using heavy browser injection to conduct a targeted attack against presumed Charles Schwab clients.
There have been several other attacks targeting specific Web site users such as LinkedIn and Apple’s iTunes over the past few weeks. Additionally, a massive attack was launched today – targeting users of the government tax services site, EFTPS.Gov a site often used by businesses to make tax payments online.















