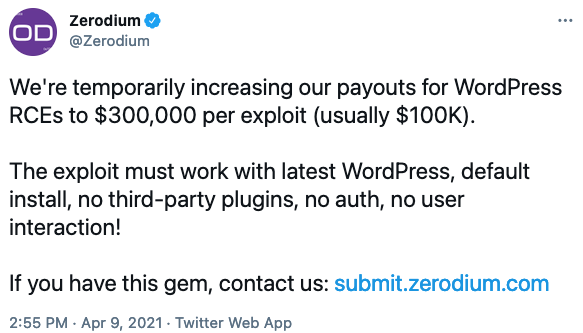
Exploit acquisition company Zerodium announced last week that it’s temporarily offering $300,000 for high-impact WordPress exploits.
The firm is looking for exploits that can be used to achieve remote code execution. The exploit must work on default configurations running the latest version of WordPress, it needs to target WordPress itself and not third-party plugins, and it must not require any authentication or user interaction.
Zerodium is prepared to pay out up to $300,000 per exploit. The company typically offers $100,000 for WordPress RCE exploits, the same amount as for Webmin, Plesk, and cPanel/WHM exploits.
Zerodium claims its customers are government organizations — mainly from North America and Europe — that seek “advanced zero-day exploits and cybersecurity capabilities.”
“At ZERODIUM we take ethics very seriously and we chose our customers very carefully, which means that access to your research and exploits will be highly restricted and limited to a very small number of institutional customers,” the company says on its website.
Exploit brokers like Zerodium are often controversial due to the possibility that they could sell their services — some of them have been caught doing so — to oppressive regimes that are likely to use them to identify and silence their critics. However, to date, there have been no reports of Zerodium offering its services to such regimes.
Currently, Zerodium offers the highest payouts for remote code execution exploits targeting Windows ($1 million), and exploits that can give a remote attacker full control of mobile devices ($2.5 million for Android and $2 million for iOS).
It’s not uncommon for the company to temporarily increase payouts for certain exploits — likely if there is a big demand — but the company is also known to stop buying certain types of exploits altogether due to surplus.
Related: Jailbreak Tool Updated to Unlock iPhones Running iOS 13.5
Related: Increased Focus on iOS Hacking Leads to Drop in Exploit Prices
Related: Zerodium Expects iOS Exploit Prices to Drop as It Announces Surplus














