A critical remote code execution vulnerability patched recently by Microsoft in Windows Remote Desktop Services (RDS) poses a serious risk to industrial environments, experts have warned.
Microsoft’s Patch Tuesday updates for May 2019 resolve nearly 80 vulnerabilities, including a flaw that can be exploited by malware to go from one device to another similar to how WannaCry spread back in 2017.
This security hole, tracked as CVE-2019-0708, impacts RDS (formerly Terminal Services) and it allows an unauthenticated attacker to take control of a device without any user interaction. The flaw can be exploited by sending specially crafted requests to the targeted machine’s RDS via the Remote Desktop Protocol (RDP).
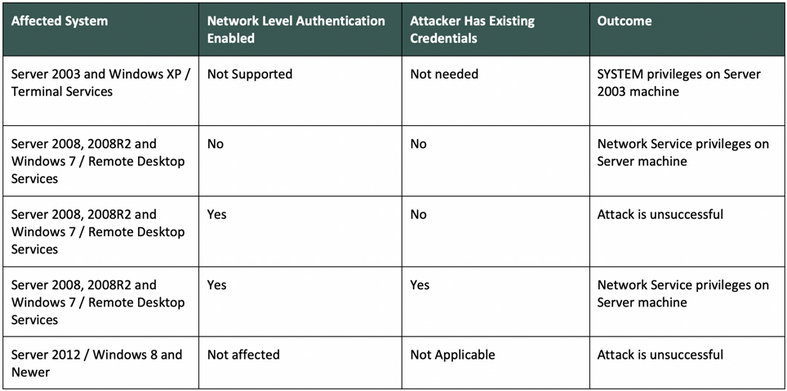
Microsoft has released patches for Windows 7 and Windows Server 2008, along with Windows XP and Windows Server 2003, which are no longer supported. Windows 8 and Windows 10 are not affected. Users of Windows 7 and Server 2008 can block unauthenticated attackers from exploiting the flaw by enabling Network Level Authentication (NLA). The threat can also be mitigated by blocking TCP port 3389 at the perimeter firewall.
The vulnerability, reported to Microsoft by UK’s National Cyber Security Centre (NCSC), has reminded many experts of the weakness leveraged by the EternalBlue exploit, which the WannaCry ransomware used in 2017.
The flaw poses a serious risk to organizations around the world and some experts have warned that industrial environments are particularly exposed as many use RDS for remote access to control systems.
Industrial cybersecurity firm Dragos has pointed out that networks housing industrial control systems (ICS) are at greater risk of attacks due to the fact that they often rely on machines running old versions of Windows and they receive updates less frequently. The company has noted that systems such as OPC servers, human-machine interfaces (HMIs) and engineering workstations all run on Windows.
Dragos has also highlighted that while enabling NLA is a good defense measure, it can be bypassed if the attacker has somehow stolen legitimate credentials.
“Exploitation of the vulnerability has not yet been observed in the wild. However, Microsoft has a working proof of concept, and it is likely adversaries will incorporate this vulnerability into attacks soon,” Dragos analysts said in a blog post.
“In ICS, system reliability is crucial, and taking machines offline to receive patches means experiencing potential downtime and loss of production, and potentially, revenue. This balancing act often favors foregoing necessary security updates in order to keep operations up and running. But patches for some vulnerabilities such as CVE-2019-0708 or MS17-010 (patches for WannaCry) are vital to apply,” they added. “Asset owners and operators should test Microsoft’s recently released patches on test devices and then patch production devices as soon as possible. This is especially important for DMZ Jump Box systems, which may have exposure to corporate networks and would be the initial ICS entry point for any future worm which uses this vulnerability.”
Boston-based IoT and ICS security company CyberX has analyzed over 850 production operational technology (OT) networks worldwide and found that 53% of them still house devices running unsupported versions of Windows, including many affected by CVE-2019-0708.
“The problem stems from the fact that patching computers in industrial control networks is challenging because they often operate 24×7 controlling large-scale physical processes like oil refining and electricity generation,” Phil Neray, VP of Industrial Cybersecurity at CyberX, told SecurityWeek. “For companies that can’t upgrade, we recommend implementing compensating controls such as network segmentation and continuous network monitoring.”
Manufacturers of industrial products have also started warning customers about CVE-2019-0708. Siemens this week informed users that its Healthineers medical products are based on Windows or they run on Windows and they may be affected by the vulnerability. The company says it’s investigating the impact of the flaws on its products.
Related: Industrial Systems at Risk of WannaCry Ransomware Attacks
Related: Why WannaCry Was a Wake Up Call for Critical Infrastructure Security













