Google has always had a sharp nose for rising Internet trends. Just recently, the search giant announced that it had acquired VirusTotal, an anti-malware start-up company to beef up protection for its Internet services.
![]() VirusTotal is a website that provides free scanning of files for viruses. It currently uses up to 44 different ant-virus products to scan the files, uploaded by the site’s users. As a result, the site holds a vast database of both malicious and benign files, uploaded to the site by its user community.
VirusTotal is a website that provides free scanning of files for viruses. It currently uses up to 44 different ant-virus products to scan the files, uploaded by the site’s users. As a result, the site holds a vast database of both malicious and benign files, uploaded to the site by its user community.
Google realized that the lack of a community based reputation feed was a key a gap in their offering and filled that hole with this acquisition.
The Social Engineered Malware Infection Challenge
When hackers try to infect a victim’s computer with malware, they have two main options to do so.
The first is by using a vulnerability exploit, by thus tricking some software component (E.g. browser/OS/plug-in) to execute malicious content without the user consent. For example, a malicious shell code embedded within a PDF that exploits vulnerabilities within Adobe’s Reader.
The second is using social engineering – tricking the user to install this program. Some common social engineering tricks are the “Fake Anti Virus” and the “Fake CODEC” scams. In the “Fake Anti Virus” scam, the malicious site displays a message “you are infected with a virus, you can cure your machine by installing the following AV software”, when actually the promised “AV software” is a malware. In the “Fake CODEC” scam, the malicious site promises some multimedia content (usually a movie of an adult nature). When the user attempts to watch the content, the site displays a message “in order to watch the video you must upgrade your player”. Once more, the “player upgrade” is actually a malware.
While from a technical point of view, the exploit option may seem to be the cooler option of the two, studies show that users are four times more likely to be tricked into downloading malware than be compromised by an exploit.
Fighting Socially Engineered Malware Infections with a Community Based Reputation Feed
Modern browsers protect their users from malware infections, by including reputation feeds. While URL reputation feeds have some success against exploit based infections, they prove to have very little success against social engineering based infections, as depicted below, where IE 9 is the obvious exception.
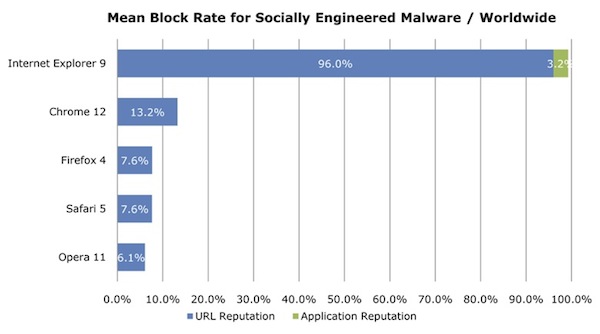
Figure 1- NSS labs results from August 2011.
What makes IE 9 so successful in stopping social engineering based infections? The SmartScreen filter technology. A key element in the SmartScreen filter technology is a community based reputation feed. The IE browser allows its users to share their file download information automatically and anonymously to the benefit of the whole community. With that, the community gets warned not only against known bad files, but also on previously unknown files. Since the malware masquerades itself as a legitimate and popular software, it’s highly unreasonable for it to be the first time it was downloaded. Therefore, it is very efficient and helpful mechanism in mitigating social engineering based infections.
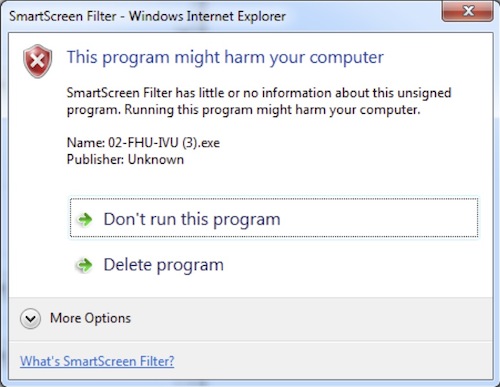
In buying VirusTotal, Google provided itself with an access to a community based reputation feed. They will probably leverage this valuable data in order to provide Chrome’s and other Google services’ users with better malware protection.
The acquisition of VirusTotal by Google signals that community based reputation feeds is a key element in a modern protection suite. We should expect the offering of such feeds soon in all of the different areas of security.












