Researchers from two universities in Germany have developed a tool that can be used to check web browsers for cross-site leaks, and they claim to have identified 14 new attack classes.
Cross-site leaks, also known as XS-Leaks, are a type of browser side-channel attack that can allow a malicious website to infer and collect potentially sensitive user information from other sites by bypassing security mechanisms such as same-origin policy.
Same-origin policy is designed to restrict how a document, script or media file loaded by one origin can interact with a resource from another origin. However, over the years, researchers have identified many methods that can be used to bypass this security mechanism.
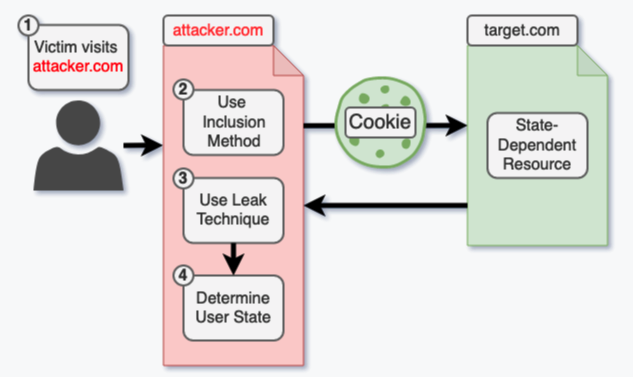
Researchers from Ruhr-Universität Bochum and Niederrhein University of Applied Sciences recently tested a total of 56 browser and operating system combinations against 34 XS-Leak methods, including methods related to status code, redirects, API usage, page content, and HTTP headers.
The researchers devised a formal model for XS-Leaks and showed how the model can be leveraged to gain an in-depth understanding of the root cause of a vulnerability. This model also led to the discovery of the 14 new attack types.
They have also developed an open source tool, named XSinator, that can be used to test a web browser. The researchers have also set up a website that shows the results of the tests they have conducted against various versions of Chrome, Firefox, Edge, Safari, Opera, Samsung Internet, and Tor Browser on desktop and mobile platforms.
In some cases, the cross-site leak attacks work against newer versions of a browser, while in other cases the older versions of a browser are impacted. The findings have been reported to impacted vendors.
The researchers have proposed new types of mitigations for preventing these types of attacks.
Related: Chrome 94 Update Patches Actively Exploited Zero-Day Vulnerability
Related: Google Patches 19 Vulnerabilities in Chrome 95 Browser Refresh
Related: Websites Can Exploit Browser Extensions to Steal User Data














