Researchers have shown how hackers could weaponize programmable logic controllers (PLCs) and use them to exploit engineering workstations running software from several major industrial automation companies.
PLCs can be a tempting target for threat actors as they can be abused to cause damage and disruption, and to make changes to the processes they control. This is why they are often seen as the ultimate goal of an attacker.
However, researchers at industrial cybersecurity firm Claroty wanted to show that PLCs can also be used as a point of entry into an organization, being leveraged to target the engineering workstations connected to them and from there the rest of the internal network.
In such an attack, named ‘Evil PLC Attack’, the hacker first compromises the PLC, which can often be exposed to the internet and unprotected, and then tricks an engineer into connecting to the PLC from the engineering workstation. This could be achieved by causing a fault on the PLC, which an engineer would likely want to investigate.
During this research, vulnerabilities have been discovered in engineering workstation software from ABB (B&R Automation Studio), Emerson (PAC Machine Edition), GE (ToolBoxST), Ovarro (TwinSoft), Rockwell Automation (Connected Components Workbench), Schneider Electric (EcoStruxure Control Expert) and Xinje (XD PLC Program Tool).
Nearly a dozen CVE identifiers have been assigned to the vulnerabilities. Over the past year and a half, impacted vendors have been releasing advisories to inform their customers about the flaws and associated patches and mitigations.
“In most cases, the vulnerabilities exist because the software fully trusted data coming from the PLC without performing extensive security checks,” Claroty noted.
The vulnerabilities found by Claroty are triggered when an engineer initiates an upload procedure. This includes transferring metadata, configurations and textcode from the PLC to the workstation. In the case of an Evil PLC attack, the data transferred from the PLC is crafted so that it triggers the security hole and executes malicious code on the workstation. Once the workstation has been compromised, the attacker can move to other systems on the network.
Learn more about vulnerabilities in industrial systems at
SecurityWeek’s ICS Cyber Security Conference
The researchers have described three different theoretical Evil PLC attack scenarios. In the first scenario, the attacker weaponizes a PLC for initial access to an organization. Specifically, the hacker takes control of an internet-exposed PLC and weaponizes it by downloading their code on the device. The attacker then causes a fault to attract the attention of engineers, whose workstation will get exploited when they connect to the PLC in an effort to diagnose it.
In a second theoretical attack scenario, the attacker targets third-party engineers and contractors, which Claroty describes as ‘traveling integrators’. In this scenario, the attacker initially compromises a PLC in a less secure facility that is known to be managed by a system integrator or contractor. The hacker weaponizes the PLC and causes a fault to get the target to connect to the device with their own workstation, which they carry with them to their different job sites. If the attacker can compromise the workstation from the less protected PLC, they can then use that workstation to hack PLCs in other, more secure organizations working with the same contractor.
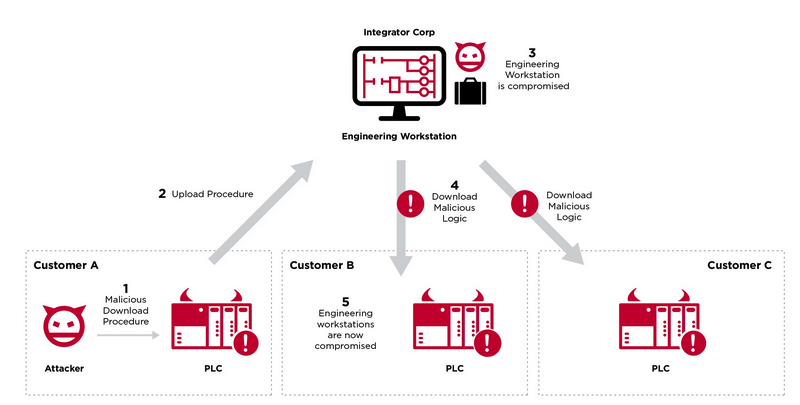
Researchers and defenders can also leverage the Evil PLC method against threat actors. They can set up a honeypot where an internet-facing PLC they have weaponized acts as a lure. When a malicious actor connects to the PLC from their own computer and attempts to obtain the currently loaded project from the controller, their device will get compromised.
“This method can be used to detect attacks in the early stage of enumeration and might also deter attackers from targeting internet-facing PLCs since they will need to secure themselves against the target they planned to attack,” Claroty researchers said.
The cybersecurity firm has shared technical details and mitigations for these types of attacks.
Related: Hackers Knew How to Target PLCs in Israel Water Facility Attacks
Related: Hack Exposes Vulnerability of Cash-Strapped US Water Plants
Related: PLC and HMI Password Cracking Tools Deliver Malware














