Vulnerabilities affecting CodeMeter, a popular licensing and DRM solution made by Germany-based Wibu-Systems, can expose industrial systems to remote attacks, industrial cybersecurity company Claroty warned on Tuesday.
CodeMeter is designed to protect software against piracy and reverse engineering, it offers licensing management capabilities, and it includes security features that provide protection against tampering and other attacks.
CodeMeter can be used for a wide range of applications, but it’s often present in industrial products, including industrial PCs, IIoT devices, and controllers.
CodeMeter is the successor of WibuKey, a DRM solution that in the past was found to expose industrial products from Siemens and other vendors to attacks due to the existence of potentially serious vulnerabilities.
Researchers at Claroty have discovered six vulnerabilities in CodeMeter, some of which could be exploited to launch attacks against industrial control systems (ICS), including to shut down devices or processes, deliver ransomware or other malware, or to execute further exploits.
Two of the security holes have been classified as critical, while the rest are considered high severity.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
Claroty reported its findings to the vendor in February and April 2019, and updates released throughout 2019 patched some of the vulnerabilities. CodeMeter 7.10, which Claroty says patches all of the reported issues, was released in August 2020.
The industrial cybersecurity firm’s researchers found various types of flaws in CodeMeter, including memory corruption bugs and cryptographic flaws that can be leveraged to alter or forge license files. They showed how some of the vulnerabilities can be exploited remotely without authentication to launch denial-of-service (DoS) attacks or achieve arbitrary code execution.
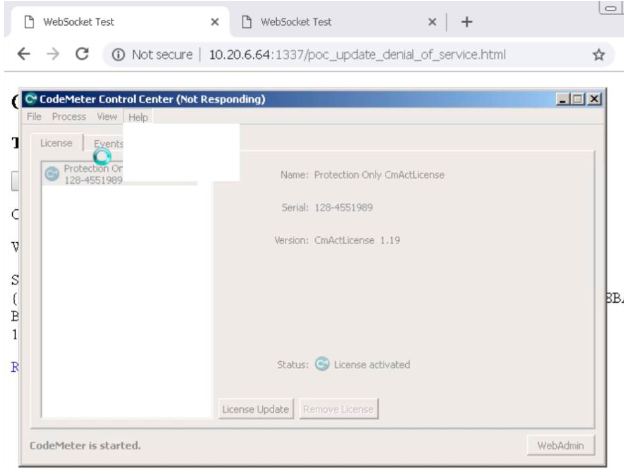
In one attack scenario described by the researchers, an attacker sets up a website designed to push a malicious license to the devices of users lured to the site. The rogue license, when processed by CodeMeter, can generate a DoS condition or allow the attacker to execute arbitrary code.
In a different attack scenario, the experts achieved remote code execution by creating their own CodeMeter API and client, which enabled them to send commands to any device running CodeMeter.
Security advisories for the CodeMeter vulnerabilities found by Claroty have also been published by Wibu-Systems and the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
Siemens and Rockwell Automation have also released advisories describing the impact of these vulnerabilities on their products.
Claroty has created an online tool that allows users to check if they are running a vulnerable version of CodeMeter. The company has also set up a GitHub page for this project.
Related: Industrial Systems Can Be Hacked Remotely via VPN Vulnerabilities
Related: Over 70% of ICS Vulnerabilities Disclosed in First Half of 2020 Remotely Exploitable
Related: Mitsubishi Patches Vulnerabilities Disclosed at ICS Hacking Contest














