Vodafone has launched an investigation after a cybercrime group claimed to have stolen hundreds of gigabytes of source code from the telecoms giant.
The hacker group, calling itself “Lapsus$,” claims to have obtained roughly 200 Gb of source code files, allegedly representing approximately 5,000 GitHub repositories.
In an emailed statement, Vodafone confirmed that it’s aware of the claims and said an investigation has been launched.
“We are investigating the claim together with law enforcement, and at this point we cannot comment on the credibility of the claim,” Vodafone told SecurityWeek. “However, what we can say is that generally the types of repositories referenced in the claim contain proprietary source code and do not contain customer data.”
The hackers haven’t leaked any of the Vodafone source code they claim to have obtained. Instead, they are asking the tens of thousands of users subscribed to their Telegram channel if they should leak source code from Vodafone, Portuguese media giant Impresa, or e-commerce firm MercadoLibre. The poll will end on March 13.
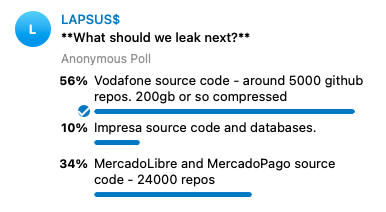
The attack on Impresa caused significant disruption, and MercadoLibre recently confirmed in an SEC filing that source code and the data of 300,000 users was compromised.
In February, Vodafone Portugal blamed some service disruptions on a “malicious cyberattack,” but it’s unclear if the incidents are related.
The Lapsus$ group recently also claimed to have stolen source code and other information from NVIDIA and Samsung.
NVIDIA has confirmed that the attackers have stolen employee credentials and code-signing certificates.
Samsung, from which the cybercriminals allegedly stole 190 GB of data, has confirmed the theft of source code related to Galaxy devices, but said that customer and employee information did not appear to have been compromised.
The hackers are hoping to get big ransom payments from the impacted companies in return for not leaking the stolen information. In the case of NVIDIA, they also demanded that the company open source drivers and remove a feature that limits the Ethereum mining capabilities on some of its graphics cards.
The attacks do not appear to involve any file-encrypting ransomware.
Related: French Ministry of Justice Targeted in Ransomware Attack
Related: Conti Ransomware Source Code Leaked
Related: University Project Cataloged 1,100 Ransomware Attacks on Critical Infrastructure















