The rating given by Uber drivers to their passengers could have been accessed until a few hours ago by simply pasting a piece of JavaScript code into a Web browser’s console.
Uber is an increasingly popular mobile application that allows users to instantly book a private car or taxi. The app enables users to rate their drivers, but the drivers themselves can also rate passengers. However, under normal circumstances, passenger ratings are directly available only to other drivers.
On Monday, software enginner Aaron Landy published a blog post containing instructions on how passengers could see their ratings by simply logging in to their accounts and executing a piece of JavaScript code in the Web browser console. After running the code, which makes a call to the Uber Web API, users were presented with a pop-up window containing their name, email address and passenger rating.
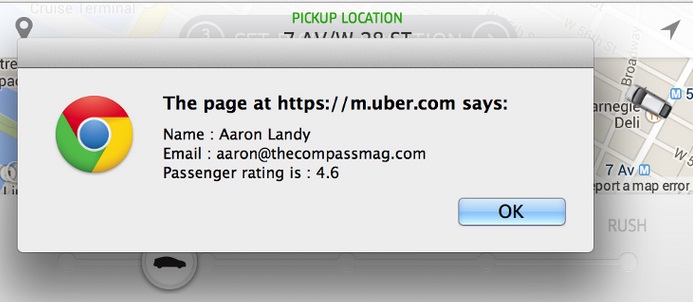
A large number of users reported on Twitter that they had found their rating before Uber took some steps to block the hack.
Contacted by SecurityWeek, Uber refused to provide any explanation as to why it wants to prevent users from exploiting this trick. Instead, the company pointed us to a blog post published in April called “Feedback is a two-way street.”
“An Uber trip should be a good experience for drivers too – drivers shouldn’t have to deal with aggressive, violent, or disrespectful riders. If a rider exhibits disrespectful, threatening, or unsafe behavior, they, too, may no longer be able to use the service,” Uber explained in the post.
The company said at the time that it had been “exploring ways to show the rider’s rating in the next generation of the app.” In the meantime, it advised users to obtain their rating by asking the driver or by contacting customer support.
While this hack might have seemed harmless for many people, some Hacker News readers pointed out the security risks of copying and pasting a random script without fully understanding it. Scammers often use such methods to trick Internet users into handing over access to their online accounts. Facebook has even published an advisory to warn customers about these self-XSS scams.














