A financially motivated cybercrime group has exploited a zero-day vulnerability in the popular file archiving utility WinRAR to deliver malware to traders and steal their money, according to cybersecurity firm Group-IB.
The vulnerability, tracked as CVE-2023-38831, was quickly patched by WinRAR developers, with a beta version released on July 20 and a stable version (6.23) on August 2. However, evidence indicates that the flaw has been exploited by threat actors since at least April 2023.
The attacks and the exploitation of CVE-2023-38831 were discovered by researchers at Group-IB. The malicious campaign was spotted on July 10 and a subsequent analysis revealed that it involved exploitation of a zero-day.
The vulnerability is related to how WinRAR processes ZIP files and it allows attackers to execute malicious code by getting the targeted user to open a specially crafted archive. The malicious archive can be disguised as a harmless .txt or .jpg file, which increases the chances of successful exploitation.
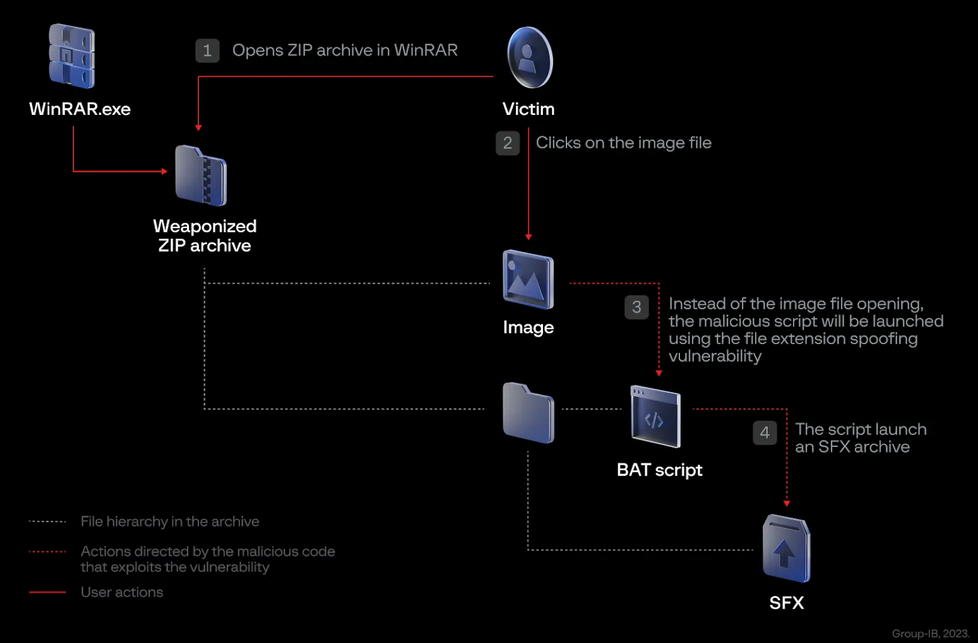
Group-IB researchers have seen these malicious archives delivering various pieces of malware, including ones known as GuLoader, Remcos RAT, and DarkMe.
The cybercriminals posted the archives on at least eight popular trading forums in an effort to get traders to install malware on their systems. The cybersecurity firm said it’s unclear how many people had their systems infected, but it had been aware of 130 infected devices at the time of its disclosure on Wednesday.
In some cases, the administrators of the targeted trading forums attempted to take action against the accounts used by the attackers, but that did not appear to discourage them.
On infected systems, Group-IB said, the hackers gained access to the victim’s broker accounts and attempted to conduct unauthorized transactions and withdraw funds. It’s unclear how much money they managed to steal. However, at least in some cases, the cybercriminals caused very small losses, such as $2.
“We have no evidence to confirm that the opening of the archive and the unauthorized access to the account are related, but we strongly believe that this is no coincidence,” Group-IB noted.
One of the pieces of malware delivered in this campaign, DarkMe, was previously observed in an operation dubbed DarkCasino that had been linked to a threat group called Evilnum.
Evilnum has been around for a long time and in recent years it was observed targeting financial technology companies, mainly ones located in Europe. The timing and political nature of a recent campaign were aligned with Russia’s invasion of Ukraine. This suggests that Evilnum is a hack-for-hire group.
On the other hand, Group-IB noted, “Although we did identify the DarkMe Trojan, which is allegedly associated with Evilnum and is distributed together with a widely-used remote access tool, we cannot conclusively link the identified campaign to this financially motivated group. It is highly probable that similar tools from the same developer can be found on underground forums.”
The news comes just days after the disclosure of CVE-2023-40477, a different WinRAR vulnerability that can be exploited for arbitrary code execution by getting the targeted user to open a specially crafted file.
While WinRAR is a highly popular piece of software, it’s not often that we hear of exploited vulnerabilities. CISA’s Known Exploited Vulnerabilities Catalog only lists one flaw: CVE-2018-20250, which hackers exploited a few years ago to deliver malware.
Related: WinRAR Vulnerability Exploited to Deliver New Malware
Related: Recently Patched WinRAR Flaw Exploited in APT Attacks
Related: Evilnum Cyberspies Update Arsenal in Recent Attacks
















