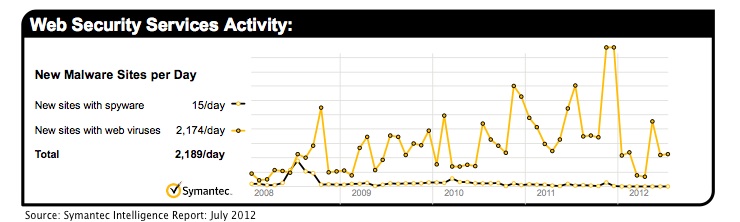
The number of malicious websites identified by Symantec has inched upward in the past month to 2,189 websites per day, according to the company’s latest intelligence report.
The figure represents a four percent increase between June and July. Some of those malicious sites have been linked to efforts to infect fans of the Olympic Games, which has been used by numerous schemes as a ploy to lure unsuspecting users – including malicious links posted on Twitter and threats bundled with Olympic-themed Android apps such as in the case of Android.Opfake.
“The Olympics is one of those rare occasions where the entire world comes together, setting aside various differences for the competition,” blogged Paul Wood, cybersecurity intelligence manager at Symantec. “The Games are a chance for each country to put their best foot forward and demonstrate their athletic skill and prowess. No doubt this spirit of goodwill generates a significant amount of excitement for athletes and spectators alike when it comes around every four years. Unfortunately, it’s exactly this goodwill that attackers are attempting to prey upon.”
The global ratio of email-borne viruses in email traffic dropped to one in 340.9 emails in July, a slight decrease of .023 percentage points since June. Last month, 26.5 percent of email-borne malware had links to malicious sites, an increase of 1.5 percent compared to June.
In terms of geography, the Netherlands remained the area with the highest ratio of malicious email activity during the month, with one in 82.2 emails identified as malicious. That ratio was one in 216.6 emails in the U.K. and one in 553.3 emails in the United States.
The most spammed industry sector was education, which had a spam rate of 70.3 percent. The second most spammed industry was the automotive sector, with 69 percent. The three most common spam categories are: newsletters (57.22 percent), dating (23.46 percent) and pharmaceuticals (12.87 percent).
The public sector remained the most targeted by phishing activity with one in 113.3 emails comprising a phishing attack, the firm found. Phishing levels for the chemical and pharmaceutical sector reached one in 1,119.1 and one in 285.9 for the financial industry.
“The number of phishing Web sites created by automated toolkits increased by approximately 12.9 percent, accounting for approximately 63.8 percent of phishing Web sites, including attacks against well-known social networking Web sites and social networking apps,” the report notes.
“The amount of attack toolkit activity on the threat landscape is now three times the average for the last six months of 2011,” Wood explained. “While the appearance and end result of such attacks has remained the same from an end-user point of view, there is a definite shift taking place in terms of how these attack toolkits are set up and administered. In the past toolkits were purchased as self-contained applications in underground marketplaces, the exploits used are now being sold as plugins for toolkit frameworks or the entire exploit process, hosting webserver included, is simply being rented out as a service.”
The report can be downloaded here in PDF format.
















