There has been a surge in ESXiArgs ransomware attacks in the past days, but it’s still not clear exactly which vulnerability is being exploited by threat actors.
In fact, questions linger over several aspects of these attacks, including who may be behind them and the origins of the malware delivered by the hackers.
In ESXiArgs attacks, an unidentified threat group has been delivering ransomware to unpatched VMware ESXi servers, encrypting files and dropping ransom notes instructing victims to pay up. While the ransom notes also inform victims that their files have been stolen, researchers have not found any evidence of data theft.
The Censys and Shodan search engines currently show 1,000-2,000 compromised ESXi servers. The number of hacked systems can be determined because the ransom notes dropped on each system are accessible directly from the internet.
The US Cybersecurity and Infrastructure Security Agency (CISA) reported seeing 3,800 compromised servers as of February 8, but that number has likely grown significantly in the past week.
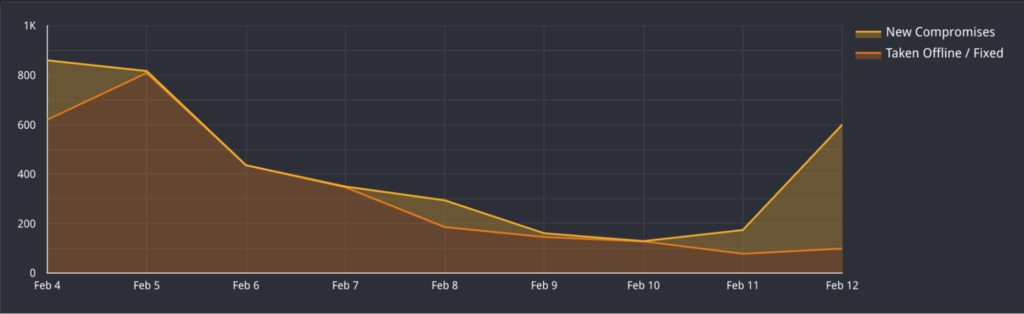
Censys reported on Wednesday that it had seen a surge in attacks, with more than 500 newly infected hosts observed on February 11-12, mainly in European countries such as France and Germany.
An analysis conducted by Censys revealed the existence of two servers that hosted ransom notes similar to the one delivered in ESXiArgs attacks in October 2022. The notes delivered in October 2022 were similar, but different. However, the two servers were updated by attackers on January 31, 2023, with a ransom note more similar to the current campaign.
It’s worth pointing out that the ransom notes are similar to the ones delivered in ransomware attacks involving Cheerscrypt, a Linux-based ransomware seen targeting ESXi servers since the spring of 2022. The base code of Cheerscrypt is derived from leaked Babuk source code.
While the attacks seen in October 2022 may have been part of a Cheerscrypt campaign, Censys noted that Cheerscrypt ransom notes were typically not accessible from the internet — like in the case of ESXiArgs attacks. As a result, Censys believes the October 2022 attacks may have been a precursor to the current campaign.
The first ESXiArgs ransomware attacks were seen on February 2, with the first warnings issued the next day.
While it has been largely assumed that the ESXiArgs attacks have exploited an ESXi OpenSLP-related vulnerability tracked as CVE-2021-21974 — which VMware patched in February 2021 — this has yet to be confirmed.
Threat intelligence company GreyNoise said last week that there is not enough evidence that CVE-2021-21974 is the only flaw being exploited. It pointed out that several OpenSLP-related vulnerabilities have been found in ESXi in recent years, and any of them could have been exploited in the ESXiArgs attacks, including CVE-2020-3992 and CVE-2019-5544.
In an update on Tuesday, GreyNoise said it had checked its records for evidence of older CVE-2021-21974 exploitation attempts and it did find two attempts between January and June 2021, but the source IPs were only active for a single day.
VMware has also highlighted that it cannot confirm which vulnerability is being exploited but said it does not appear to be a zero-day.
“VMware currently has no evidence to support that a new vulnerability is being used to propagate recent ransomware attacks, but there is also no evidence that CVE-2021-21974 is the only attack vector, either,” the virtualization giant said in an FAQ document focusing on ESXiArgs.
“The media has speculated about the involvement of CVE-2022-31699, CVE-2021-21995, CVE-2021-21974, CVE-2020-3992, and CVE-2019-5544 but it is very likely that the attackers are using any vulnerability that is accessible to them. VMware is continuing to investigate,” it added.
As attackers continue to launch ESXiArgs attacks, they also continue improving the malware. Initial versions left some files unencrypted, allowing some users to recover their files without paying a ransom. CISA even released an open source recovery tool to help impacted organizations.
However, newer versions of the malware encrypt more data, and since researchers have yet to find a weakness in the actual encryption method, recovering the files becomes an impossible task, at least for now.
Malware targeting ESXi servers has been increasingly common over the past few years. Threat intelligence company Recorded Future reported recently that it saw a three-fold increase in ransomware attacks targeting ESXi between 2021 and 2022, including Alphv, LockBit and Black Basta.
Related: VMware Confirms Exploit Code Released for Critical vRealize Logging Vulnerabilities















